Zscaler experts report that hackers are again stealing from hackers, as it turned out that the creator of the malware, Prynt Stealer, equipped his creation with a backdoor. With the help of this “bookmark”, Prynt Stealer makes a copy of all the data stolen from the victim and leaks information not only to its operators, but also to the author of the malware.
یادآوری کنم که ما هم همین را نوشتیم غیر معمول YTSstealer بدافزار یوتیوبرها را هدف قرار می دهد, و همچنین آن این ModernLoader RAT Trojan Is Used to Infect Systems with Stealers and Cryptominers.
For the first time, Prynt Stealer, based on the sources of AsyncRAT and the StormKitty infostealer, came to the attention of information security experts back in April 2022. Then the malware was studied by analysts from سیبل. They said that the malware has broad capabilities, comes with additional keylogger and clipper modules, and is advertised as a solution for compromising a wide variety of browsers, instant messengers, and gaming applications, and is also capable of carrying out direct financial attacks.
Prynt Stealer is a subscription service and the author is asking $100/month, $200/quarter, or $700/year, and also offers a lifetime license for $900.
Back in the spring, it was reported that data stolen by Prynt Stealer is usually compressed and transmitted to malware operators via a تلگرام bot. با این حال, as researchers from Zscaler now write, Prynt Stealer contains a backdoor: the malware comes with an additional hard-coded token and Telegram ID, and the data stolen from the victims is also sent to the malware author.
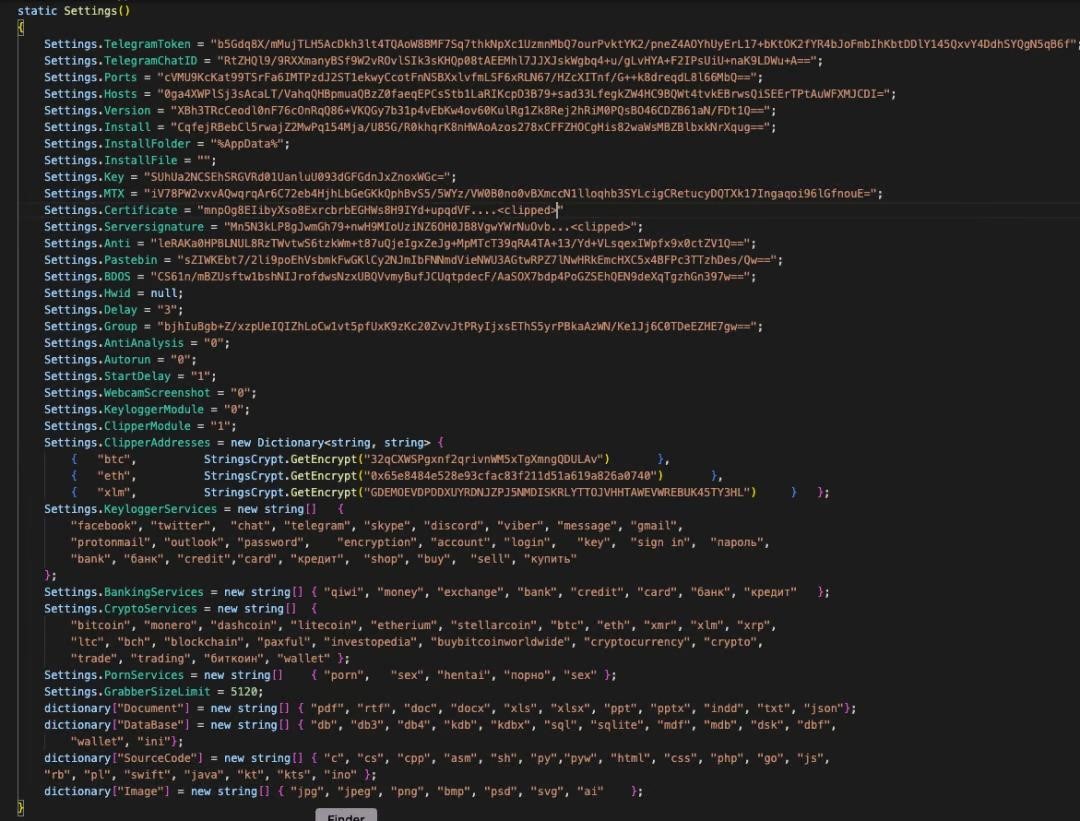
DarkEye token,Telegram ID and the keylogger code
Zscaler analysts note that Prynt Stealer may be related to more than just AsyncRAT and StormKitty mentioned above. They also found a connection with the WorldWind and DarkEye malware families, and suggest that the same author may be behind these malware.
After examining a leaked copy of the Prynt Stealer builder, the researchers found that during execution, the loader extracts DarkEye Stealer from اختلاف نظر and configures it to transfer data to the malware author. در حقیقت, DarkEye is a variant of Prynt Stealer, and the difference between them is only in the enabled or disabled clipper and keylogger functions.
علاوه بر این, the author of Prynt Stealer configured the builder in such a way that it loads and executes LodaRAT. This is an old but powerful Trojan dating back to 2017 that allows a remote attacker to take full control of the infected system, steal information, inject additional payloads, و غیره.
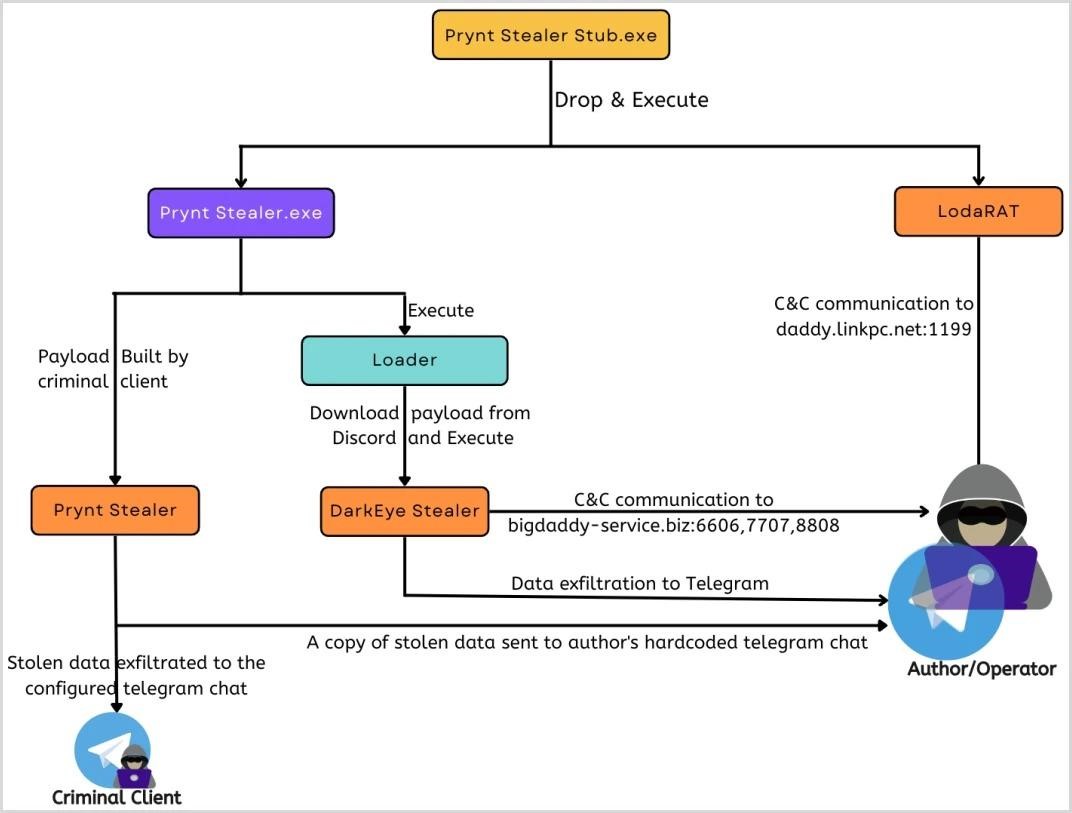
Scheme of infection
The researchers suggest that after this exposure, Prynt Stealer will lose the bulk of its customers. با این حال, it seems that the malware creator has two new products on the way, and at present it is almost not advertised on hacker forums.

پیام بگذارید