Intel is investigating hackers’ claims that they have stolen MSI’s private keys used by the Intel Boot Guard. The fact is that such a leak may affect the ability to block malicious UEFI versions on MSI devices.
As it became known in early April 2023, the extortionate group Money Message announced that the Taiwanese manufacturer MSI (Micro-Star International) had been hacked. According to media reports, extortionists stole approximately 1.5 TB of data from the company and demanded a ransom of $4,000,000.
The attackers wrote that they had at their disposal “the MSI source code, including the BIOS development framework”, as well as “private keys that allow you to sign any custom module of this BIOS and install it on a PC with this BIOS.”
Przypomnę, że to też pisaliśmy Secure Boot Is Not Working on MSI Motherboards for over a Year. Also the media wrote that Fake MSI Afterburner Infects Users’ Machines with Miners and Stealers.
As Bleeping Computer now reports, the hackers did not receive a ransom from the company and began to publish stolen information in the public domain, including the source code for the firmware used by MSI motherboards.
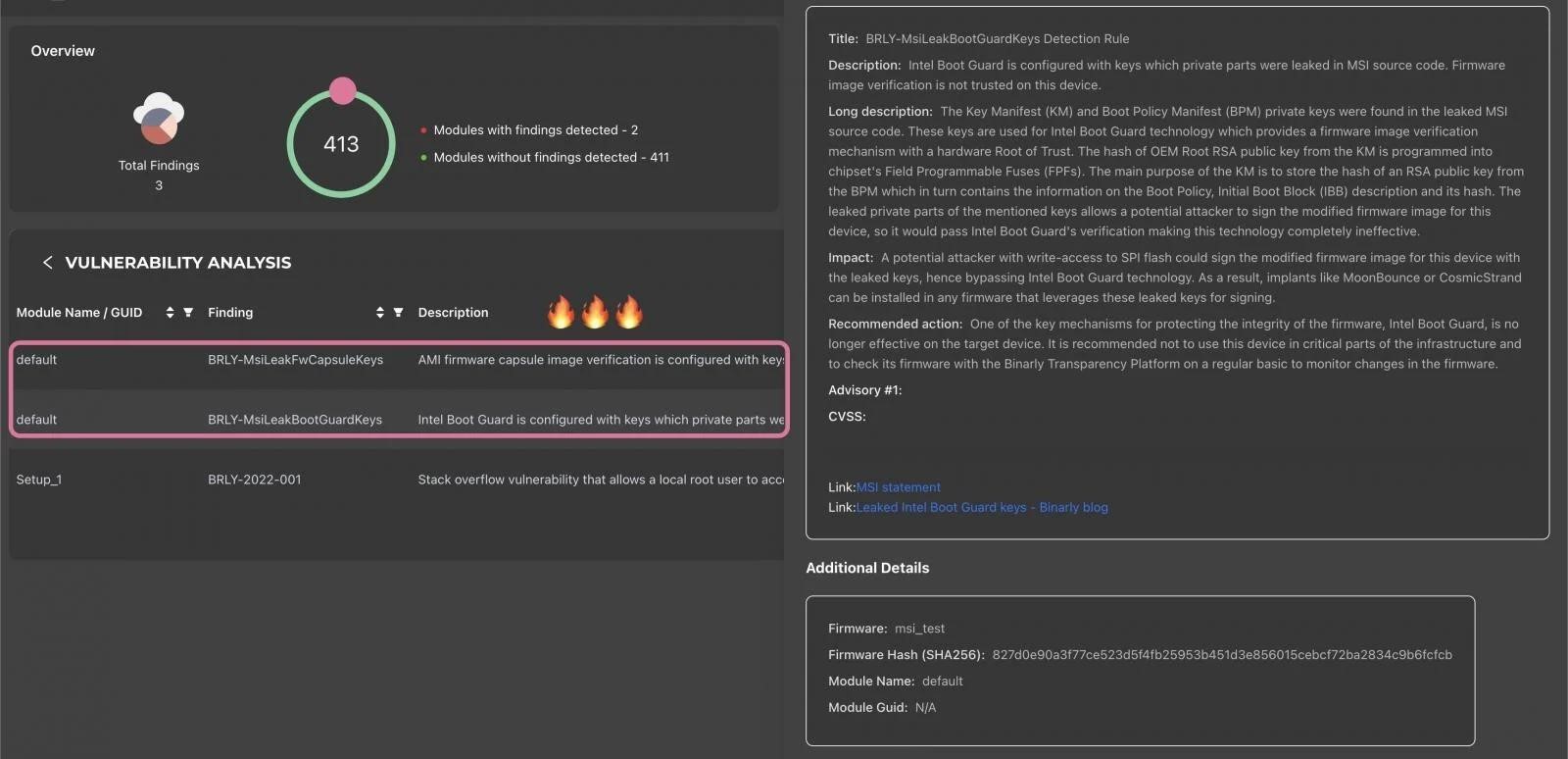
Late last week, Binarly CEO Alex Matrosov warned that the leak contained image signing private keys Do 57 MSI products and Intel Boot Guard private keys for 116 MSI products.
Matrosov explains that such a leak could result in Intel Boot Guard not working on MSI devices using Tiger Lake, Adler Lake, and Raptor Lake processors. Dodatkowo, MSI’s Boot Guard keys appear to be affecting several device manufacturers, including Intel, Lenovo, I Supermicro.
The protective function Intel Boot Guard, built into modern Intel hardware, is designed to prevent the loading of malicious firmware, that is, UEFI bootkits, and is one of the main requirements of Windows UEFI Secure Boot.
The fact is that malicious firmware is loaded before the OS is loaded, which allows it to hide its activity from security software and remain present on the device even after reinstalling the operating system. To protect against this, Intel Boot Guard verifies that the firmware image is signed with a legitimate private signing key using the public key built into the Intel hardware.
The worst thing about the leak is that the public keys used to verify firmware signed with the now compromised keys are embedded in the Intel hardware. If they cannot be changed, Intel Boot Guard protection can no longer be relied upon.
Intel representatives told the media that they are aware of these expert warnings, and the company is already conducting its own investigation.
Supermicro representatives say they have also looked into the potential risks associated with this leak, and the company is confident that its products are not affected.
Binarly analysts have already published a list of affected MSI hardware, which includes 116 devices compromised as a result of leaked Intel Boot Guard keys.

Zostaw komentarz