Cyble researchers discovered a trojanized installer for Super Mario 3: Mario Forever for Windows that infected unsuspecting players with numerous malware.
Super Mario 3: Mario Forever is a free version of the classic Nintendo game developed by Buziol Games and released for Windows in 2003. Since then, the development of the game has continued, several versions have been released with bug fixes and improvements, and today the game is still popular and considered a classic.
Let me remind you that we also wrote that Erbium Infostealer Is Spreading under the Guise of Cracks and Cheats for Games, and also that Unusual YTStealer Malware Targets YouTubers.
Read also an interesting review of information security specialists: 5 Dangers of Cracked Games.
Experts from the Cyble company discovered that the attackers created a modified installer for Super Mario 3: Mario Forever, which is presented as a self-extracting executable archive and distributed through unknown channels. Most likely, the infected game is advertised on game forums, social networks, or offered to users through malicious advertising, black hat SEO, and so on..
Malicious installer
The archive contains three executable files, one of which installs the game itself (super-mario-forever-v702e.exe) and the other two (java.exe og atom.exe) are silently installed in the AppData directory during game installation.
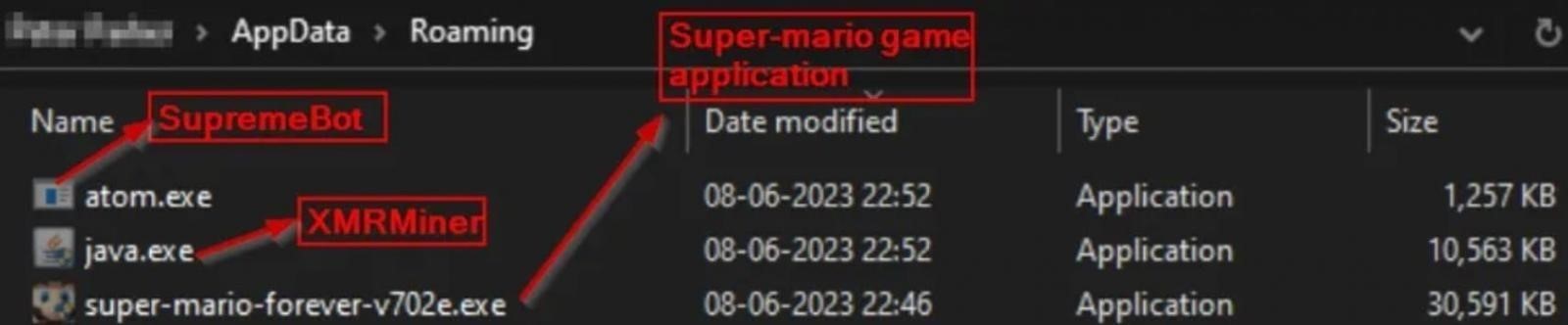
Once the malicious executables are on disk, the installer launches them to launch the XMR (Monero) miner and the SupremeBot mining client.
The java.exe file is a Monero cryptocurrency miner that collects information about the victim’s hardware and connects to the gulf[.]moneroocean[.]stream server to get started.
SupremeBot (atom.exe) creates a copy of itself and places it in a hidden folder in the game’s installation directory. Neste, it creates a scheduled task to execute this copy, which runs every 15 minutes indefinitely, hiding under the name of a legitimate process.
This terminates the original process and deletes the original file to avoid detection. The malware then establishes a connection to the command and control server to transfer system data, register a client, and receive configuration in order to start mining Monero. After that, SupremeBot also receives an additional payload from the server (in the form of an executable named wime.exe).
This last file is an open source Umbral Stealer infostealer written in C# and available on GitHub since April 2023. It steals information stored in browsers from an infected device, including saved passwords and cookies containing session tokens, cryptocurrency wallet data, as well as credentials and authentication tokens for Discord, Minecraft, Roblox og Telegram.
I tillegg, Umbral Stealer can bypass Windows Defender by disabling the program if tamper protection is not enabled. Otherwise, it adds itself to the exclusion list. The malware also modifies the hosts file to disrupt the operation of popular antivirus products and the websites of the respective companies, preventing normal operation.
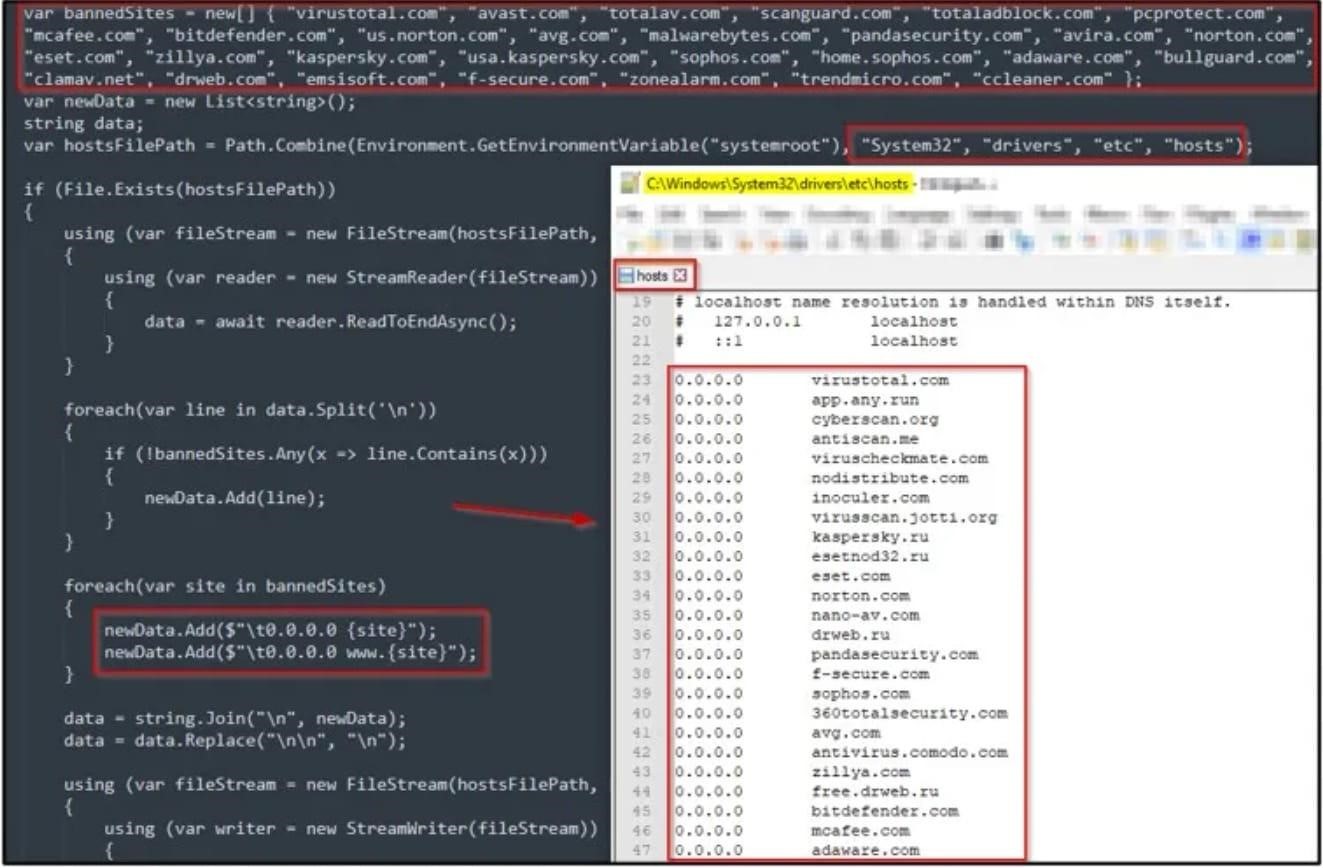
Changes in hosts
The stealer is also able to take screenshots of the victim’s desktop and use webcams connected to the system. Before being sent to the attackers’ server, all stolen data is stored locally.
The researchers recommend that anyone who has recently downloaded Super Mario 3: Mario Forever check their computer for installed malware and remove it if any is found.

Legg igjen en kommentar