A new Trojan for Windows, recently discovered on the cyber threat landscape, steals passwords stored in the Google Chrome browser. At the same time, the malware uses a remote MongoDB database to store the stolen credentials.
MalwareHunterTeam research team discovered the Trojan named CStealer, and they noted the malware’s unusual approach to sending collected passwords.
A new Windows trojan has been discovered, it attempts to steal passwords stored in the Google Chrome browser. While this is nothing unique, what stands out is that the malware uses a remote MongoDB database to store the stolen passwords”, — report IS researchers from MalwareHunterTeam.
As noted above, CStealer is interested in the credentials stored in Google Chrome’s built-in password manager. However, one nuance sets this malware apart from other similar Trojans.
Instead of compiling passwords into a single file and sending it to a C2 server, which is under the control of cybercriminals, CStealer directly connects to the MongoDB database, and subsequently uses it to store stolen credentials.
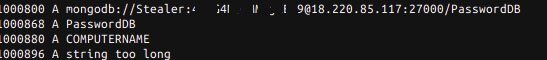
As can be seen from the screenshot provided by MalwareHunterTeam researchers, the database name and password are hardcoded in the malware code, and the MongoDB C Driver library is used to connect.
While this method ultimately serves its purpose of stealing passwords, it also opens the door for other attackers to gain access to the victim’s credentials”, — report BleepingComputer journalists citing data from MalwareHunterTeam.
The main danger of this approach is that anyone with the opportunity to analyze the CStealer code (law enforcement, researchers, cybercriminals) will be able to calculate hard-coded database data, which will allow access to the stolen passwords of the victims.
Note that not only attackers producing Trojans and stealers target Windows users. Researchers at Devcon recently published a report on the analysis of malicious advertising. According to experts, most advertising campaigns (approximately 61%) target Windows users.
Read also: TPM-FAIL Vulnerabilities Threaten PCs, Laptops, Servers, and Other Devices
According to experts, the reason for such a high attractiveness of Windows for various cybercriminal groups is the huge market share of this system, so majority of the malware over the past 30 years targeted Windows devices.

Leave a Comment