Unknown attackers attack Russian organizations using the Woody Rat Trojan, which allows to remotely control infected devices and steal information from them.
A new Remote Access Trojan (RAT) was discovered Malwarebytes analysts, who dubbed the malware Woody Rat. According to them, one of the victims of the new malware was the Russian aircraft corporation United Aircraft Corporation (UAC).
Woody Rat has a wide range of capabilities and has been used in attacks for at least a year. Currently, the malware is delivered to victims’ computers via phishing emails: using ZIP archives containing a malicious payload, or via Microsoft Office documents entitled “Information Security Memo” that use the Follina vulnerability to deploy payloads.
Let me remind you that we also reported that Malware Roaming Mantis Devours Thousands of Devices around the World, and also that Windows Trojan steals passwords from Chrome and stores them in MongoDB database.
The list of features of the Woody Rat Trojan includes collecting system information, listing folders and running processes, executing commands and files received from the control server, uploading, downloading and deleting files on infected machines, as well as creating screenshots.
In addition, Woody Rat is able to execute .NET code, PowerShell commands and scripts that it receives from its management server using two DLLs (WoodySharpExecutor and WoodyPowerSession).
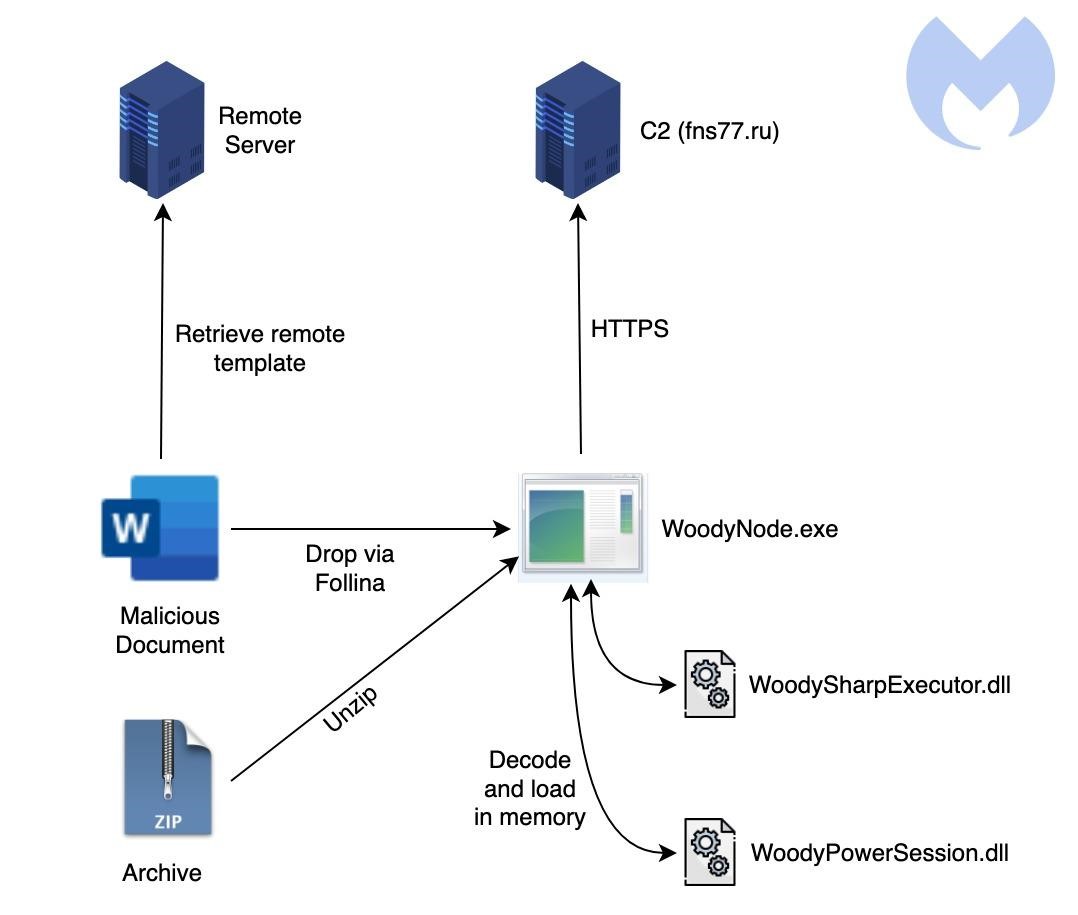
Running on a compromised device, the malware uses the process hollowing technique to infiltrate the suspended Notepad process, then remove itself from disk to avoid detection.
RAT encrypts its communications with the C&C infrastructure using a combination of RSA-4096 and AES-CBC to avoid the attention of network monitoring tools.
Malwarebytes experts do not associate this malware and attacks with any specific hack group, but write that the list of possible suspects is extremely small, and it includes Chinese and North Korean APTs.

Leave a Comment