Representatives of the company Twilio, engaged in the development and provision of cloud PaaS services, reported that unknown attackers hacked the company and gained access to the data of some of its customers.
To do this, the attackers stole the credentials of the company’s employees by arranging a phishing attack on them via SMS.
Let me remind you that we also wrote that Hackers Start Looking for Vulnerable Endpoints 15 Minutes after They Are Discovered, and also that Hacked Software Hunters May Be Victims of FakeCrack Malware Campaign.
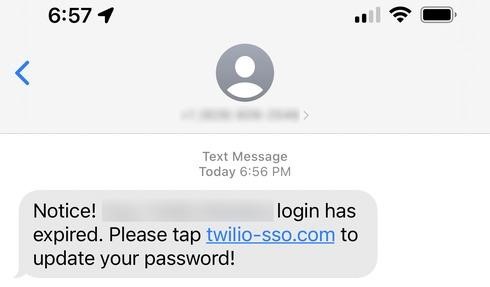
It is known that as part of a phishing attack on Twilio employees, hackers posed as representatives of the company’s IT department. In their SMS messages, they asked people to click on links containing keywords such as Twilio, Okta and SSO, after which the victims were taken to a fake Twilio login page. People were persuaded to click on malicious links with warnings that their passwords had supposedly expired or that it was time to change them according to the plan, since they were out of date.
At the same time, Twilio declined to comment and disclose additional information about the incident, without answering questions from the media about how many employees were compromised and how many customers were eventually affected by this hack. It is worth noting that Twilio has 26 offices in 17 countries, employing more than 5,000 people.
We are aware that other companies have also been subjected to similar attacks, and we have coordinated with them in response to the attackers, including working with carriers to stop the spread of malicious messages, and with registrars and hosting providers to block malicious URLs. Despite these countermeasures, the attackers continue to switch carriers and hosting providers to renew their attacks.the companies add.
It is reported that an investigation into the incident is currently underway, to which law enforcement agencies have already been involved.
Immediately after the attack was discovered, Twilio canceled compromised employee accounts to block hackers from accessing their systems and began to notify customers affected by the incident. It is emphasized that the attackers gained access to a “limited amount” of data, so affected clients are notified on an individual basis.

Leave a Comment