Flashpoint and Sekoia experts have discovered a new data-stealing malware, RisePro infostealer, which is distributed through sites with fake cracks.
These sites are built and managed using the pay-per-install (PPI) malware distribution service PrivateLoader.
Let me remind you that we also wrote that Erbium Infostealer Is Spreading under the Guise of Cracks and Cheats for Games, and also that Unusual YTStealer Malware Targets YouTubers.
The media also reported that Meta Infostealer Malware Spread via Spam.
Flashpoint and Sekoia write that RisePro is a new threat focused on stealing bank card data, passwords, and cryptocurrency wallet data from infected devices. The malware is distributed under the guise of key and crack generators for various software, as well as mods for games.
Loading on a malicious site
Flashpoint reports that malware operators have already begun selling thousands of RisePro logs (data collected from infected devices) on Russian-language marketplaces on the dark web.
Sekoia analysts say they have found significant similarities between PrivateLoader and RisePro code. They believe that the operators of the malware distribution platform have launched their own infostealer (for themselves or as a new service). RisePro is reportedly currently available for purchase via Telegram.
RisePro is written in C++ and is probably built on the source code of another infostealer – Vidar, since it uses the same DLL dependency system.
After infection, the malware scans the compromised system, carefully examines the registry keys and saves the found data to a text file and takes a screenshot. As a result, the malware packs everything collected into a ZIP archive, and then sends the archive to the attackers’ server.
RisePro tries to steal a wide range of data from apps, browsers, cryptocurrency wallets and browser extensions:
- Browsers: Google Chrome, Firefox, Maxthon3, K-Melon, Sputnik, Nichrome, Uran, Chromodo, Netbox, Comodo, Torch, Orbitum, QIP Surf, Coowon, CatalinaGroup Citrio, Chromium, Elements, Vivaldi, Chedot, CentBrowser, 7start, ChomePlus , Iridium, Amigo, Opera, Brave, CryptoTab, Yandex, IceDragon, BlackHaw, Pale Moon, Atom.
- Browser Extensions: Authenticator, MetaMask, Jaxx Liberty Extension, iWallet, BitAppWallet, SaturnWallet, GuildWallet, MewCx, Wombat, CloverWallet, NeoLine, RoninWallet, LiqualityWallet, EQUALWallet, Guarda, Coinbase, MathWallet, NiftyWallet, Yoroi, BinanceChainWallet, TronLink, Phantom, Oxygen, PaliWallet, PaliWallet, Bolt X, ForboleX, XDEFI Wallet, Maiar DeFi Wallet.
- Software: Discord, battle.net, Authy Desktop.
- Cryptocurrency assets: Bitcoin, Dogecoin, Anoncoin, BBQCoin, BBQCoin, DashCore, Florincoin, Franko, Freicoin, GoldCoin (GLD), IOCoin, Infinitecoin, Ixcoin, Megacoin, Mincoin, Namecoin, Primecoin, Terracoin, YACoin, Zcash, devcoin, digitalcoin, Litecoin, reddcoin.
In addition, RisePro can scan folders in the file system looking for interesting data, such as receipts containing bank card information.
The researchers remind that the above-mentioned PrivateLoader is a pay-per-install malware distribution service that disguises malware as cracks, key generators, and game mods. In fact, the attackers provide PrivateLoader operators with a sample of the malware they want to distribute, tell them what the targeting criteria are, and make the payment.
After that, PrivateLoader uses its network of fake and hacked sites to spread the resulting malware.
This service for hackers was discovered in the spring of 2022 by Intel471 specialists. Interestingly, until recently, PrivateLoader has been distributing only the popular infosealers RedLine and Raccoon (with rare exceptions).
Now that RisePro has added to its arsenal, Sekoia experts note that the new infostealer has the capabilities of a loader, and its code largely coincides with the code of the PrivateLoader itself. Similarities were seen in string obfuscation techniques, HTTP message obfuscation, and HTTP and port settings.
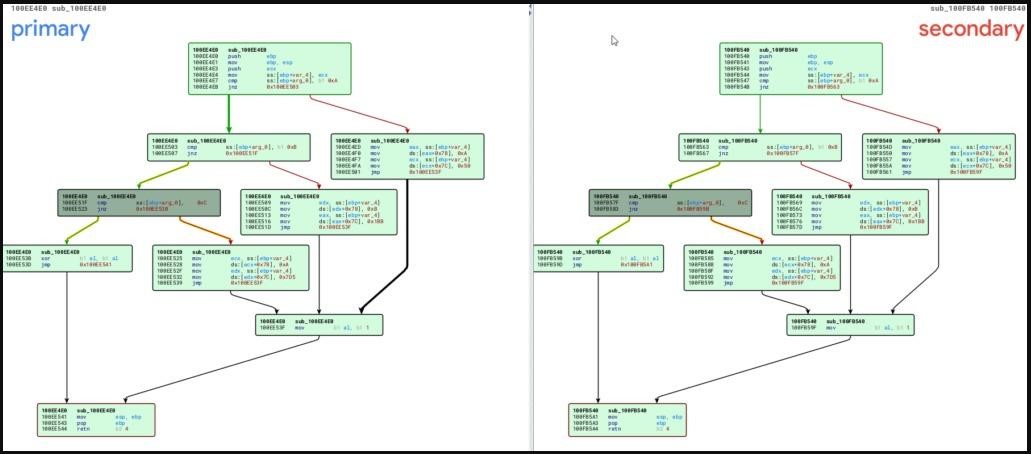
As a result, the researchers suggest that RisePro could have been developed by the same people behind PrivateLoader. Another theory says that RisePro is a new round of development of PrivateLoader itself or the “brainchild” of a former developer of the same hack group, who is now promoting his own PPI service.

Leave a Comment