According to AT&T Cybersecurity analysts, China has once again activated and used the Great Cannon, a powerful DDoS attack tool that was last used two years ago.
The Great Cannon was last used in 2017 when the Chinese authorities used it for DDoS attacks on Mingjingnews.com, a Chinese news site in New York.
Prior to this, the tool was used to organize DDoS attacks on GitHub, since they host utilities to help Chinese users bypass the national firewall, and GreatFire.org is a portal dedicated to Internet censorship around the world.
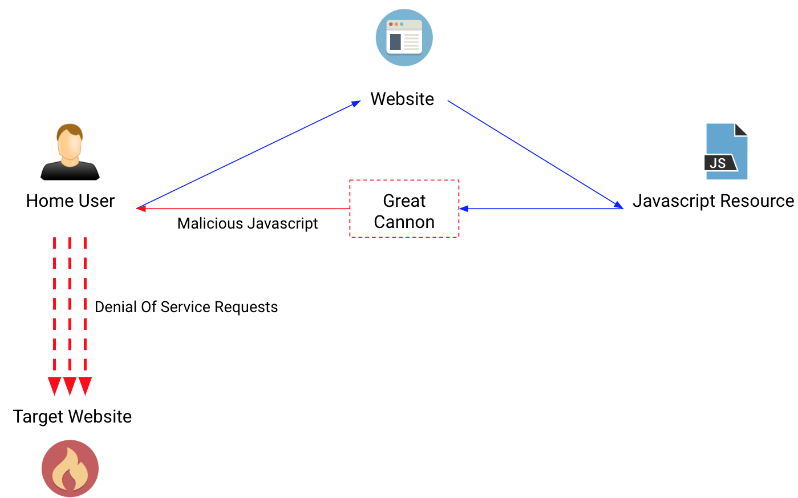
The Great Cannon is a distributed denial of service tool (“DDoS”) that operates by injecting malicious Javascript into pages served from behind the Great Firewall. These scripts, potentially served to millions of users across the internet, hijack the users’ connections to make multiple requests against the targeted site. These requests consume all the resources of the targeted site, making it unavailable”, — Chris Doman from AT&T Cybersecurity talks about the totalitarian technology in China.
According to a 2015 report compiled by Citizen Lab experts, the Great Cannon and the Great Chinese Firewall used similar codes and were located on the same servers. So, the DDoS tool intercepted traffic destined for sites located in China and inserted JavaScript into the responses received by users in browsers. This malicious JavaScript ran in browsers and secretly accessed the victim site, creating gigantic bursts of traffic.
Now AT&T Cybersecurity experts claim that the “Great Cannon” is used again. This time, the target of the attacks was LIHKG.com, an online platform where protest organizers in Hong Kong share information about the venue for daily demonstrations.
The site is also a gathering place for Hong Kong residents, where they publish stories about police abuse and download video evidence.
The first DDoS attacks on LIHKG were detected on August 31, 2019, and the last attack was recorded on November 27, 2019. The August attacks used JavaScript code very similar to the code that was discovered earlier during the attacks on Mingjingnews.com in 2017”, — writes Chris Doman.
According to the LIHKG administration, during the August attack, the site received more than 1.5 billion requests per hour, while under normal circumstances, the site traffic is only 6.5 million requests per hour.
AT&T Cybersecurity Expert Conclusions
It is unlikely these sites will be seriously impacted. Partly due to LIHKG sitting behind an anti-DDoS service, and partly due to some bugs in the malicious Javascript code.
Read also: Online trackers have learned to bypass ban on tracing Internet users
Still, it is disturbing to see an attack tool with the potential power of the Great Cannon used more regularly, and again causing collateral damage to US based services.

Leave a Comment