Facts about “Security Alert. Your accounts were hacked by a criminal group. Scam“.
Similar to the majority of other tricky spam campaigns, “Security Alert. Your accounts were hacked by a criminal group. Scam” is run and controlled by the team of online frauds who elaborate threats and pose certain ransom requirements. These alerts normally indicate that they have stolen your personal details and made a compromising video or picture of you. They pose threats mentioning that if you do not want this information to be delivered to all of your available contacts, you should initiate a ransom payment. This is a common scam and there is no need to be worried about.
Often, online frauds deliver the aforesaid emails to many victims (the figure may amount even to millions). Based on the statement of the alert, malicious code has been recently uploaded to your PC that lets cyber frauds keep records your personal data (passwords, available contacts, etc). They also mention that they have uploaded a remote access utility and that they can survey over all your actions online. In this particular instance, the crooks indicate that they have taken photos of you while you were attending “shocking” pages (allegedly, pornographic ones). It proceeds on to indicate that you shold now transfer $870 in Bitcoins, otherwise this information will be delivered to your colleagues, friends, members of your family and all other persons in your contacts. The crooks mention that you should make the payment within 48 hours. The developers of the “Security Alert. Your accounts were hacked by a criminal group. Scam” message indicate that if you do not comply with the requirements, they will lock your device and transfer the pictures to your contacts. All other online frauds apply similar approaches. We strongly advise that you simply disregard them and do not transfer any ransom amount.
| Name | “Security Alert. Your accounts were hacked by a criminal group.” spam campaign |
| Threat Type | Phishing, Scam, Social Engineering, Fraud |
| Faulty Claim | Frauds falsely indicate that they’ve injected victim’s device with a virus that collected compromising information (video) of the message recipient. They also blackmail the victim by falsely promising to transfer the video to all the victim’s contacts in case a ransom amount is not transferred. |
| Cyber Criminal Cryptowallet Addresses | 3AvVjgoYfrtbbG2repDCdcLLMcjJ73jLqm, 395wdUpmkEG6iPdCguKCqYJR5UkpdWm5Wk, 3HnDpvc9mXTcmAePPCaU3q82egxP8p5P6G, 3JgjbyQJcymqApzph5EWDQdH8cNphXFZKu, 3NmUUGnYGkMn2hAi9L8sd5J4okWjq3mZNe, 1ELKdWgfedTJ9FV4U5W2JVXFzTpKSqcCjM, 3HxqrQmEffcMZo5cgNqRXwD3dw5LCYSx7K, 1ANFoTP6ETjBfL6o3ZhJm1jag1x1KAbAxZ, 37yLxF7mM7h3KiDvqWh88wm1VjFvemDYpf, 358MfWU8MctxPJhFBiNpsdGtxDtHixTi8r, 3AVitbSbsDWRyda9JNs8avrjhq2ZN7uCMy, 15Q5a6gHDaAtqFE3uEhfAhY8PqJiaw94vT, 3FL1txfM4knPnySJHiXAsK91cnmEXHGemv, 1CMBC1Mj86GHmbwzcMMP8xUe1hQTwk4Ds7, 1Ji2K8EVzxDRnpuXts1kKAjMwTrV2LTnRS, 3QikbxiTy7cWH7ZGZbLQYANxZA2MZHmmDs, 3JPdsEkcxv715Th7hN7fgoUYds22xBaPno, 1Niyhcqd8MNT8tpRs8gK6Ho3V8fJy2wbF, 1FErgudo2nCpuu9XSLJkSiqQBy62N1weiy, 1NvwQchudHai3KcqDkwTGgNzHK9YrWHzV6, 1AfwxZ8nYzwEzME39PuqVZU7Mn73XxQTqq, 17nhAbZGm4UmSVj5Zx8amwAbjVXcxGtEAz, 1ipEif9Roe3DjboppZ99mswU6r7Y1puUi, 1Dg5UsxMEG41TC3i9ugxcFV6cVtz8cpfXE, 1DpfAYoWGpTprX3cRg6mnUuYqNm3eXiR4F, 1BcpAGfamAy81enJtHahKedaWx1yATTXT7, 1KUknkh9bC4TPUoPXv4SnKdib8RAnUXDGw, 1G3UXmDBoeRvU3D2tGmGGU7fpCAEY1dBQV, 18Jro9LNFqBQarcc63WYGf3w7PdDAiwXpk, 13WVfQkbqdsSUNBDPDWTLqSXeaYX1tZ6UD, 1MS638iFfpruXbiLA43GVuoPEBLpKQDTjd, 1EUj48o3UnZvCjZEvYX9CHYbuL7rkhnB8s |
| Amount Of Ransom | $600, $750, $870, $900 – figure varies depending on the campaign’s version. |
| Symptoms | Unapproved online purchases, amended online account credentials, identity theft, illegal access of the PC. |
| Distribution channels | Tricky emails, milsleading online pop-up advertisemetns, search engine hijacking techniques, displaying fake (improperly spelled) domains. |
| Negative impact | Loss of crucial personal data, financial loss, identity theft. |
| Elimination | To delete possible malware threats our virus researchers suggest scanning your PC with Loaris Trojan Remover .
Free scanner inspects whether your device is messed up. To delete malware, you need to buy the full version of Loaris Trojan Remover. |
Other versions of spam campaigns very identical to “Security Alert. Your accounts were hacked by a criminal group. Scam” are known under the names “Embed A Malware On The Web Page”, “Hacker Who Cracked Your Email And Device”, and “Remote Control Desktop With A Key Logger”. These are just some casual examples from many other available variants. Most spam campaigns are applied to trick the users into transferring the funds to cybercriminals, who indicate to own embarrassing or compromising information regarding the victim. In spite of this, not all scammers present ransom requirements. Some transfer emails with dubious attachments and suggest the users to open them. The attachments are normally Microsoft Office files, such as Word, Excel, PowerPoint, etc. Do not ever interact with these attached files, since they contain high-risk malware such as TrickBot, Adwind, FormBook, and other similar infections. Threats of this type might cause information loss or even financial troubles. They are often elaborated to collect people’s personal data such as bank account credentials, passwords, logins, and so on. These activities can result in various issues associated with privacy, browsing safety, finances, etc. These threats might also reveal “backdoors” for other threats, such as ransomware-type infections.
We get a great portion of feedback from scared customers regarding this scam email. Here is the most common question we get:
Q: Hi loaris.com team, I got an email indicating that that my PC was infected and they have a video file depicting me. Now they are demanding a ransom in Bitcoins. I believe this must be true because they mentioned my real name and password contained in the email. What must I do in this case?
A: Disregard this email. Neither the frauds nor cyber criminals have infected/hacked your device and there is no video of you watching pornographic information. Just disregard the alert and do not transfer any Bitcoins. Your email, name, and other important credentials were probably stolen via a hacked webpage such as Yahoo (such website breaches are quite typical).
How do spam campaigns attack PCs?
Spam campaigns that promote dubious attachments normally apply Microsoft Office files. If opened, they prompt the victims to enable macro commands, which then grants permission for viruses to be downloaded and injected. This, however, only functions with the Microsoft Office environment. In case the attachment is launched via the software other than Microsoft Office applications, the virus will not be injected. Obviously, most spam campaigns attack Windows owners who own Microsoft Office products. The clients of other operating systems (or those who are not the customers of Microsoft Office) are normally safe.
How to prevent intrusion of malware?
If you get an email from an unknown/suspicious addressee with an irrelevant attachment, do not ever open it without first carefully researching the email. Download programs by means of official and reliable resources only. Do not use any third-party software downloading clients or installers, because these are often supported by means of advertising rogue programs. Install programs with caution and make sure to always opt for “Custom”, “Advanced” installation mode, and other similar approaches. In some instances, software developers refer to the “bundling” channel, thus potentially unwanted programs are concealed within download/installation menu. Hence, update programs by means of utilities or implemented features rendered by the official developers. Faulty software updaters must not be applied, because they contain potentially unwanted, fake utilities. You are recommended to use Microsoft Office 2010 or its later versions. Older versions do not have a “Protected View” mode, which blocks downloaded documents (malicious email attachments) from downloading and installing unwanted software. If you have already launched specific malicious attachments, we suggest running a scan with Loaris for Windows to automatically delete injected threats.
The text contained in the “Security Alert. Your accounts were hacked by a criminal group. Scam” email alert:
Hello! I am a hacker who has access to your operating system. I also have full access to your account. I've been watching you for a few months now. The fact is that you were infected with malware through an adult site that you visited. If you are not familiar with this, I will explain. Trojan Virus gives me full access and control over a computer or other device. This means that I can see everything on your screen, turn on the camera and microphone, but you do not know about it. I also have access to all your contacts and all your correspondence. Why your antivirus did not detect malware? Answer: My malware uses the driver, I update its signatures every 4 hours so that your antivirus is silent. I made a video showing how you satisfy yourself in the left half of the screen, and in the right half you see the video that you watched. With one click of the mouse, I can send this video to all your emails and contacts on social networks. I can also post access to all your e-mail correspondence and messengers that you use. If you want to prevent this, transfer the amount of $500 to my bitcoin address (if you do not know how to do this, write to Google: "Buy Bitcoin"). My bitcoin address (BTC Wallet) is: 3AvVjgoYfrtbbG2repDCdcLLMcjJ73jLqm, 395wdUpmkEG6iPdCguKCqYJR5UkpdWm5Wk, 3HnDpvc9mXTcmAePPCaU3q82egxP8p5P6G, 3JgjbyQJcymqApzph5EWDQdH8cNphXFZKu, 3NmUUGnYGkMn2hAi9L8sd5J4okWjq3mZNe, 1ELKdWgfedTJ9FV4U5W2JVXFzTpKSqcCjM, 3HxqrQmEffcMZo5cgNqRXwD3dw5LCYSx7K, 1ANFoTP6ETjBfL6o3ZhJm1jag1x1KAbAxZ, 37yLxF7mM7h3KiDvqWh88wm1VjFvemDYpf, 358MfWU8MctxPJhFBiNpsdGtxDtHixTi8r, 3AVitbSbsDWRyda9JNs8avrjhq2ZN7uCMy, 15Q5a6gHDaAtqFE3uEhfAhY8PqJiaw94vT, 3FL1txfM4knPnySJHiXAsK91cnmEXHGemv, 1CMBC1Mj86GHmbwzcMMP8xUe1hQTwk4Ds7, 1Ji2K8EVzxDRnpuXts1kKAjMwTrV2LTnRS, 3QikbxiTy7cWH7ZGZbLQYANxZA2MZHmmDs, 3JPdsEkcxv715Th7hN7fgoUYds22xBaPno, 1Niyhcqd8MNT8tpRs8gK6Ho3V8fJy2wbF, 1FErgudo2nCpuu9XSLJkSiqQBy62N1weiy, 1NvwQchudHai3KcqDkwTGgNzHK9YrWHzV6, 1AfwxZ8nYzwEzME39PuqVZU7Mn73XxQTqq, 17nhAbZGm4UmSVj5Zx8amwAbjVXcxGtEAz, 1ipEif9Roe3DjboppZ99mswU6r7Y1puUi, 1Dg5UsxMEG41TC3i9ugxcFV6cVtz8cpfXE, 1DpfAYoWGpTprX3cRg6mnUuYqNm3eXiR4F, 1BcpAGfamAy81enJtHahKedaWx1yATTXT7, 1KUknkh9bC4TPUoPXv4SnKdib8RAnUXDGw, 1G3UXmDBoeRvU3D2tGmGGU7fpCAEY1dBQV, 18Jro9LNFqBQarcc63WYGf3w7PdDAiwXpk, 13WVfQkbqdsSUNBDPDWTLqSXeaYX1tZ6UD, 1MS638iFfpruXbiLA43GVuoPEBLpKQDTjd, 1EUj48o3UnZvCjZEvYX9CHYbuL7rkhnB8s After receiving the payment, I will delete the video and you will never hear me again. I give you 50 hours (more than 2 days) to pay. I have a notice reading this letter, and the timer will work when you see this letter. Filing a complaint somewhere does not make sense because this email cannot be tracked like my bitcoin address. I do not make any mistakes. If I find that you have shared this message with someone else, the video will be immediately distributed. Best regards!
Immediate automatic elimination of possible virus threats:
Manual malware elimination might be a time-consuming and complex procedure that implies extended PC knowledge. Loaris Trojan Remover is an effective and automatic virus elimination software that will help you to delete possible virus threats. Download it by means of the button provided below:

By means of downloading any program listed on this webpage you agree to our Privacy Policy and License Agreement. Free scanner inspects whether your device is damaged. To delete infections, you need to buy the full version of Loaris.
Quick menu:
How to delete infections manually?
Manual virus elimination is a complex procedure – usually it is best to let antivirus or anti-malware utilties to perform this in an automatic manner. To delete this infect we suggest using Loaris Trojan Remover. If you would like to delete the threats manually, the first milestone is to establish the name of the malware that you are attempting to delete. Here is an example of a suspicious software running on a user’s device:
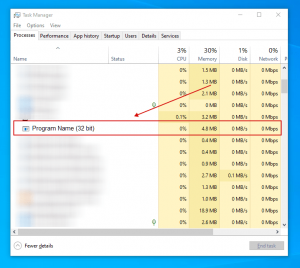
If you inspected the list of applications available on your device, for example by means of the Task Manager, and located a utility that looks unsafe, you need to proceed with these steps:
Step 1 Download a software named System Explorer. This application displays auto-start programs, Registry, and file system paths:
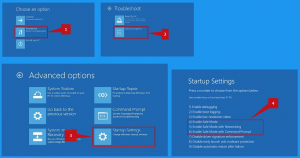
Step 2 Reboot your PC into Safe Mode:
Windows 8 users: Launch Windows 8 is Safe Mode with Networking – Proceed to Windows 8 Start Screen, specify Advanced, in the search results choose Settings. Select Advanced startup options, in the opened “General PC Settings” window, choose Advanced startup. Select the “Restart now” button. Your PC will now reload into the “Advanced Startup options menu”. Select the “Troubleshoot” button, and then choose the “Advanced options” button. In the advanced options menu, choose “Startup settings”. Select the “Restart” button. Your device will reload into the Startup Settings screen. Hit F5 to load in Safe Mode with Networking.
Windows 10 users: Click on the Windows logo and select the Power icon. In the opened menu select “Restart” while holding “Shift” button on the keyboard. In the “choose an option” window select the “Troubleshoot” area, afterwards, choose “Advanced options”. In the advanced options menu choose “Startup Settings” and select the “Restart” button. In the next window, you need to click the “F5” button on your keyboard. This will reboot your system in safe mode with networking.
Step 3 Run the SystemExplorerSetup.exe file.
Step 4 Check the list rendered by the System Explorer program and find the malware file that you need to delete.
You need to write down its full destination and name. Keep in mind that certain virus masks process names under decent Windows process names. At this point, it is very important to avoid deleting important system files. Once you establish the suspicious application you would like to delete, right click your mouse over its name and select “End Process“.
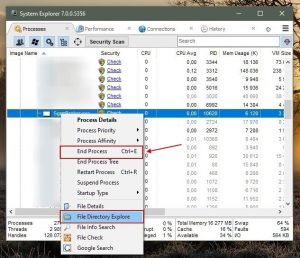
After deleting the virus via the System Explorer software (this guarantees that the virus will not launch itself automatically upon the next system startup), you need to look for the malware name on your PC. Make sure to enable hidden files and folders before you proceed. If you establish the filename of the virus, make sure to delete it.
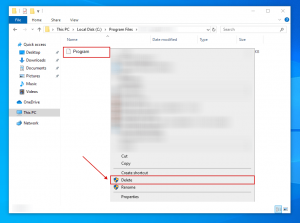
Reload your PC in normal mode. Following these milestones should delete any malware from your PC. Keep in mind that manual virus elimination requires extended PC skills. If you are not technically savvy, leave virus elimination to antivirus and anti-malware utilities. These milestones might not help with extended virus infections. As usual, it is best to avoid infections than attempting to delete the threats later on. To maintain your PC in a safe condition, install the latest operating system updates and always refer to the help of antivirus programs.

Leave a Comment