“Secure Boot Violation” tech scam that shows an alert that claims to be a Window notification. This alert indicates that your system files will be removed and claim that your system has problem.
Skip the guide and find out how to remove “Secure Boot Violation” fake Tech Support Scam!
When the “Secure Boot Violation” Scam is shown in your browser it will contain the specific text similar to the following.
A problem has been detected and Windows has been shutdown to prevent damage to your computer.The system found unauthorized changes done on your firmwire, operating system or UEFI drivers. Please enter your Systems Key to run the device or enter directly to BIOS setup if there is no other boot devices installed.
Serial Key [Submit]
If you continue to see this error message after inserting your serial key then do the following,
Visit your nearest windows authorized service center.
Contact your system administrator.
For online assistance contact windows authorized service desk on 1(855)-913-9111(Tollfree)
Error code Oxc004e016
© Microsoft Corporation 2019
Regretfully, browser-based tech support informs make it tough to shut down the display or in a lot of cases even the browser itself. Fortunately, virtually all browser-based tech assistance scams can be shut down by mosting likely to the Windows Task Manager and also shutting down the browser procedure. It is necessary to understand, though, that if you end the web browser process that you do not restore previously closed internet sites if prompted by the web browser when you launch it once again.
Furthremore, as long as common site advertisements might reveal browser tech support scams, they are also typically used by a number of adware-type applications. Hence, if you are completely running into web browser based technology support rip-offs, you require to take on scan research study of your system for adware.
“Secure Boot Violation” – Why am I Encountering?
The Secure Boot Violation Fraud is shown through ads that forward you to internet sites that reveal this scam. Such ads can be shown by installed adware applications or using less than trusted pages that are revealing them to create advertising and marketing earnings.
In the majority of the cases, if you experience a browser-based phony tech support rip-off, then you can just close down the internet browser as well as launch it again. On the other hand, if you are permanently running into scams comparable to the “Secure Boot Violation” alert, after that you require to scan your gadget for adware as well as eliminate anything that is located within your system.
Self Help Instructions
To get rid of “Secure Boot Violation” Tech Support Scam, please undertake these steps:
To shut a browser-based Tech Support Scam alert, very first check if you can close the tab it is being shown on or the browser itself. If you are unable of doing so, after that you require to adhere to the steps listed below relying on your os.
To shut down Secure Boot Violation Tech Support Scam, you should stop the process for the browser that is now showing the browser-based tech support scam. To do this we will refer to the help of the Windows Task Manager. To start the task manager, hit the Ctrl, Alt, and Delete buttons simultaneously to reveal the Windows security screen displayed below.
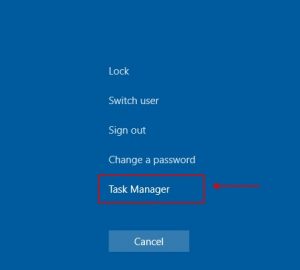
As soon as the above message is open, click on the Task Manager link as shown by the red arrow in the picture shown above.
The Windows Task Manager will now open and show all the active programs on the device as displayed below.
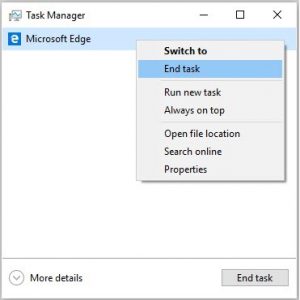
Browse via the list of running programs and left-click once on the task related to your web browser. The names for an active browser could specify Microsoft Edge,Internet Explorer, Chrome, Opera and Firefox.
As soon as you have chosen a browser task, click on the End Task button to shut down the program and the browser tech support scam.
You need to shut all browser tasks as soon as the window displaying the technology support rip-off is closed down.
The next time you start your internet browser, do not allow the web browser to present the last opened site. You can currently go to the next steps.
To shut down Your Windows 7, Windows Vista is damaged and irrelevant Tech Support Scam, you should stop the process for the browser that is now showing the browser-based tech support scam. To do this we will apply the Windows Task Manager. To launch the task manager, hit the Ctrl, Alt, and Delete buttons simultaneously to obtain the Windows security message displayed below.
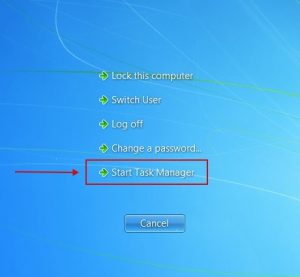
At the above screen, click on the Task Manager option to launch the Windows Task Manager.
When Task Manager is launched you will be in the Applications area as displayed below.
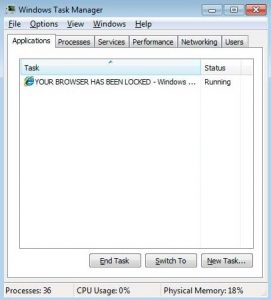
Right now, you need to select the Processes tab.
You will now end up at a screen that displays the active processes on your device. Click on the button revealed Show processes from all users as displayed in the picture below.
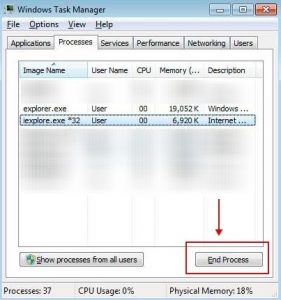
Afterwards, check the list until you encounter your web browser’s process and left-click on it as soon as it gets highlighted. As soon as you choose the browser’s process, click on the End Process button as displayed by the red arrow in the image above. If you are uncertain of the process name to terminate, please have a look at the table below:
| When you are using this browser: | Terminate this process: |
|---|---|
| Internet Explorer | iexplore.exe |
| Chrome | chrome.exe |
| Safari | Safari.exe |
| SeaMonkey | seamonkey.exe |
| Opera | opera.exe |
| Firefox | firefox.exe |
As soon as you click on the End Process button, Task Manager will ask you to prove if you are sure you would like to shut it down as displayed in the image below.
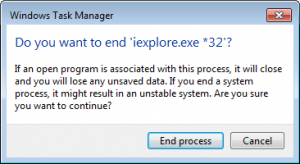
Right now, you need to click on the Yes button for the purpose of killing the process.
Your browser window must now be shut down. The next time you start your browser, do not permit the browser to open the last opened website. You may now go to the next steps.
In order to stop any applications that may complicate the removal procedure we should first download the Rkill application. Rkill will inspect your device for available virus threats and try to stop them so that they would not prevent the removal procedure. For this purpose, you need to download RKill to your device via the following link.
As soon as it is downloaded, double-click on the iExplore.exe icon. This way, you will automatically try to terminate any processes related to Secure Boot Violation Tech Support Scam and other threats. Please take your time while the application searches for various malware apps and terminates them. As soon as this has been done, the black window will automatically shut down and a log file will come up. You need to review the log file and then shut down so you can proceed with the next step.
If you have issues using RKill, you can download the other renamed versions of RKill via the rkill download page. All of the files stand for renamed copies of RKill, which you can use instead. Please bear in mind that the download page will come up in a new browser window or tab.
Do not restart your device after running RKill as the malware applications will be launched again.
Right now, you should download Loaris Trojan Remover, for the purpose of scanning your device for any any viruses, adware, or potentially unwanted applications that may be in place. Go ahead and download Loaris Trojan Remover via the following location and save it to your desktop:
You will at this point be at the main screen for Loaris Trojan Remover as displayed below.
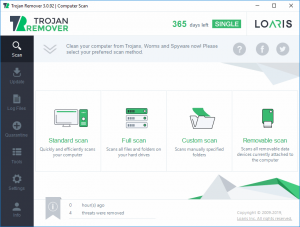
Choose the Full Scan button to start the malware elimination scan.
Loaris will now begin scanning your device for viruses, adware, and potentially unwanted applications. This procedure can take quite a continuous time, so we offer you do something else and from time to time check on the stage of the scan to check when it is over.
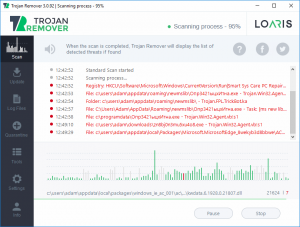
As soon as Loaris has completed scanning it will show a screen that notifies of any applications that have been removed. Please keep in mind that the applications detected may be different than what is displayed in the image below.
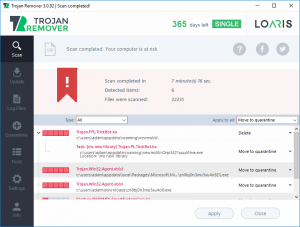
Inspect the scan results and when you are ready to proceed with the cleanup procedure, click on the Apply button to remove or repair all of the the chosen results.
We recommend that you reset your browser settings with the help of Trojan Killer Portable. For this puprose, perform the following steps.
Download Trojan Killer Portable by clicking on the button below:
Install and start the program. Click on the icon in the form of the globe to open the built-in utility to reset your available browsers:
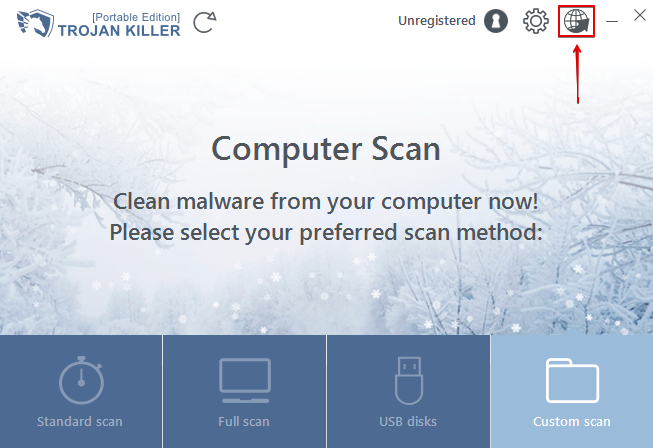
Icon to open the utility to reset browser settings with Trojan Killer
Select the browsers you would like to reset and the available reset options. Finally, click on the “Reset” button:
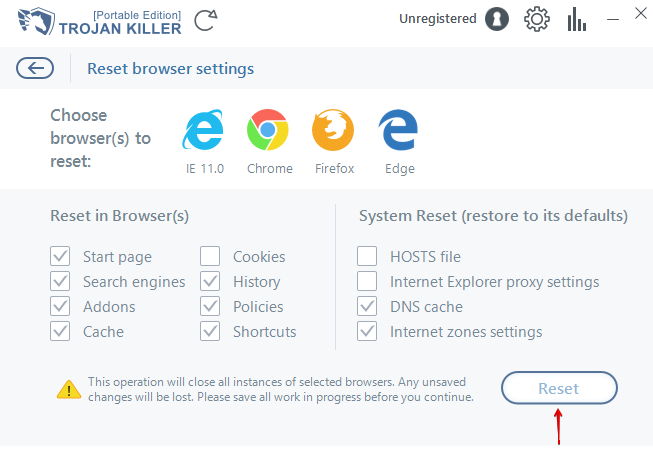
“Reset” button
Once the process is completed, you will encounter the following message:
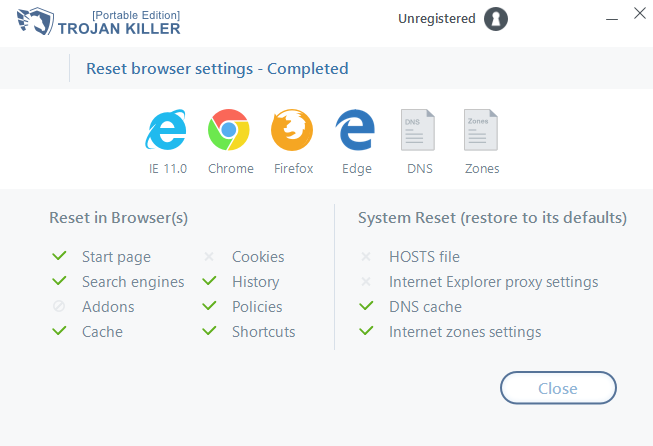
Reset complete
Your system should now be fixed and the ‘Secure Boot Violation Tech Support Scam’ issue should be resolved. In case your present anti-malware tool permitted this utility on your device, consider buying the full version of Loaris Trojan Remover to get the defence against these kinds of infections in the future.
If you are still experiencing issues with your computer after meeting these guidelines, please do not be reluctant to contact us using remarks.



Leave a Comment