A New Zealand student accidentally discovered that on 290 models of MSI motherboards, the Secure Boot function, which is responsible for UEFI secure boot, does not work by default.
This means that any OS image can be run on vulnerable machines, regardless of whether it is signed and whether the signature is genuine.
Let me remind you that we also reported that Vulnerability in iOS and macOS Allowed Eavesdropping on Siri Conversations, and also that Boa’s Forgotten Web Servers Become a Threat to Critical Industries.
The media also reported that Serious new vulnerabilities threaten Intel processors.
Dawid Potocki spoke about his discovery about MSI motherboards in his personal blog. According to him, he discovered the problem by accident while setting up a new computer.
It turned out that back in January 2022, MSI, with the release of a new firmware, changed the settings in the Secure Boot section in its UEFI / BIOS, changing the default values.
So, now all the values in the Image Execution Policy subsection were set to Always Execute (“Always execute”). This means that even if the malware has modified the OS bootloader, the MSI UEFI/BIOS will still boot the malicious image, even if there is clearly something wrong with its cryptographic signature.
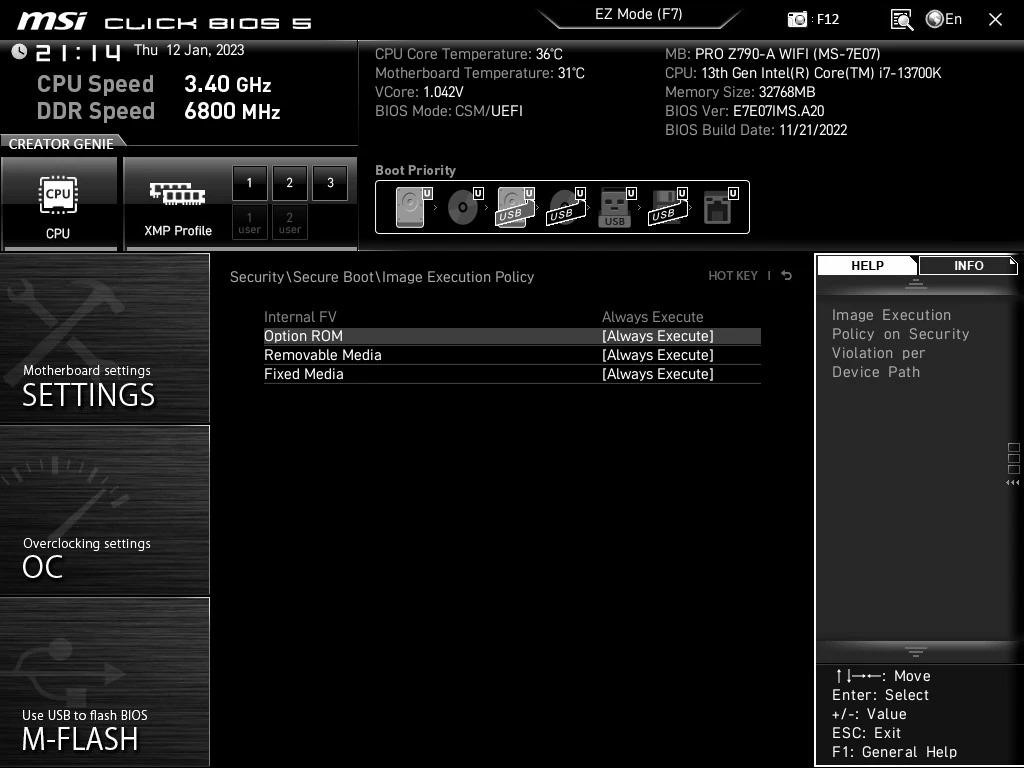
Pototsky writes that the settings, of course, need to be changed to more reasonable ones, setting the Deny Execute value to at least Removable Media and Fixed Media. As for changing the Option ROM settings, the researcher advises reading additional information first.
However, after discovering the problem on his machine, Potocki went further and decided to find out if only his motherboard had undergone such “improvements” by the MSI developers, and it turned out that the problem was much larger.
It turned out that the manufacturer changed the settings to unsafe for more than 290 motherboard models (for both Intel and AMD processors), a complete list of which can be found here.
For all users of MSI motherboards, Potocki recommends checking the settings and, if necessary, setting the values in the Image Execution Policy section to safe ones.

Leave a Comment