Researchers from HUMAN’s Satori Threat Intelligence team discovered and interrupted a massive Vastflux fraudulent campaign involving malicious ads. Within its framework, more than 1,700 applications from 120 publishers (mostly for iOS) were forged and about 11 million devices were affected.
Let me remind you that we reported that Vulnerability in iOS and macOS Allowed Eavesdropping on Siri Conversations, as well as Hackers Persuade Victims to Install Copybara Android Malware.
And also the media reported that was Revealed a fraudulent scheme, due to which millions of Android smartphones are quickly discharged.
The Vastflux campaign was discovered by accident while investigating a single ad fraud scheme. For example, the researchers noticed that an unnamed popular iOS app generates an unusually high number of requests using different app IDs.
By reversing the obfuscated JavaScript that was running in the application, the experts found the IP address of the control server, as well as the commands sent by the server to create ads. According to the researchers, at this stage, they fell into “a rabbit hole that got deeper and deeper.”
The company report states that Vastflux operators generated bid requests to display banner ads in apps (at the peak of the campaign, their number reached 12 billion per day). If their request won, they placed a static banner in which obfuscated JavaScript was injected.
These scripts contacted the command and control server to receive an encrypted settings payload that included instructions on the position, size, and type of ads displayed behind the banner, as well as data to spoof real app and publisher IDs.
Vastflux operators placed up to 25 video ads on top of each other, all of which generated ad revenue for them, although none of the ads were visible to the user as they were displayed outside the active window.
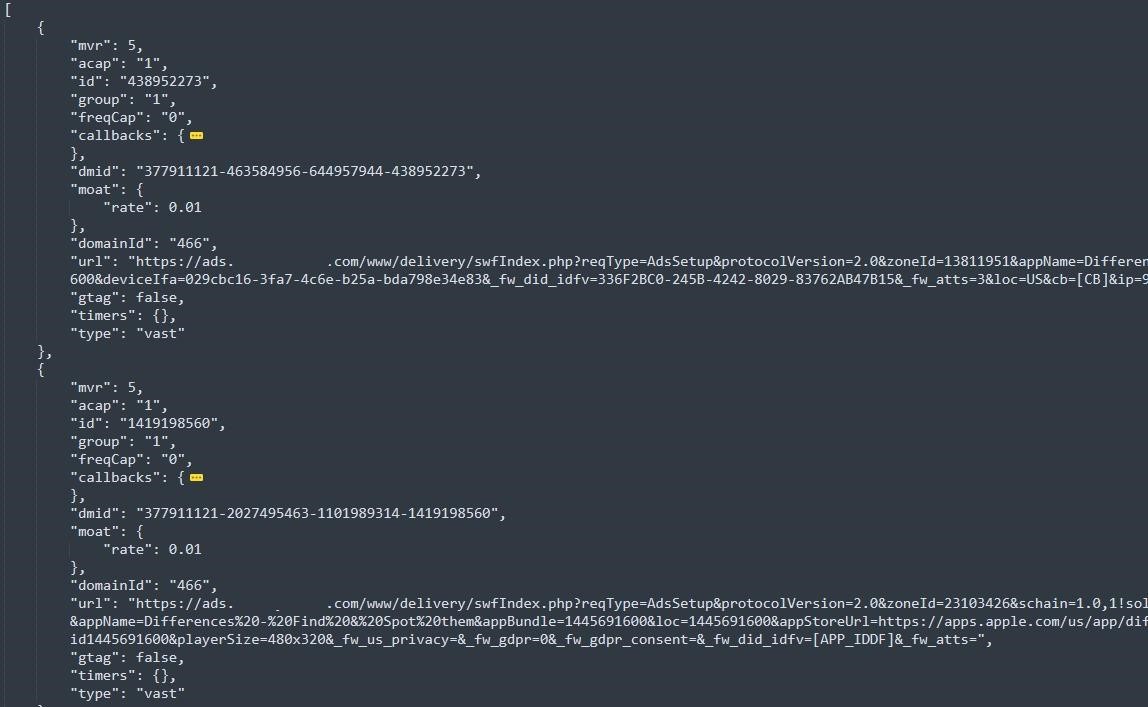
To avoid detection, Vastflux did not use ad verification tags, which allow marketers to create performance metrics. Without them, this scheme became virtually invisible to most third-party ad performance tracking tools.
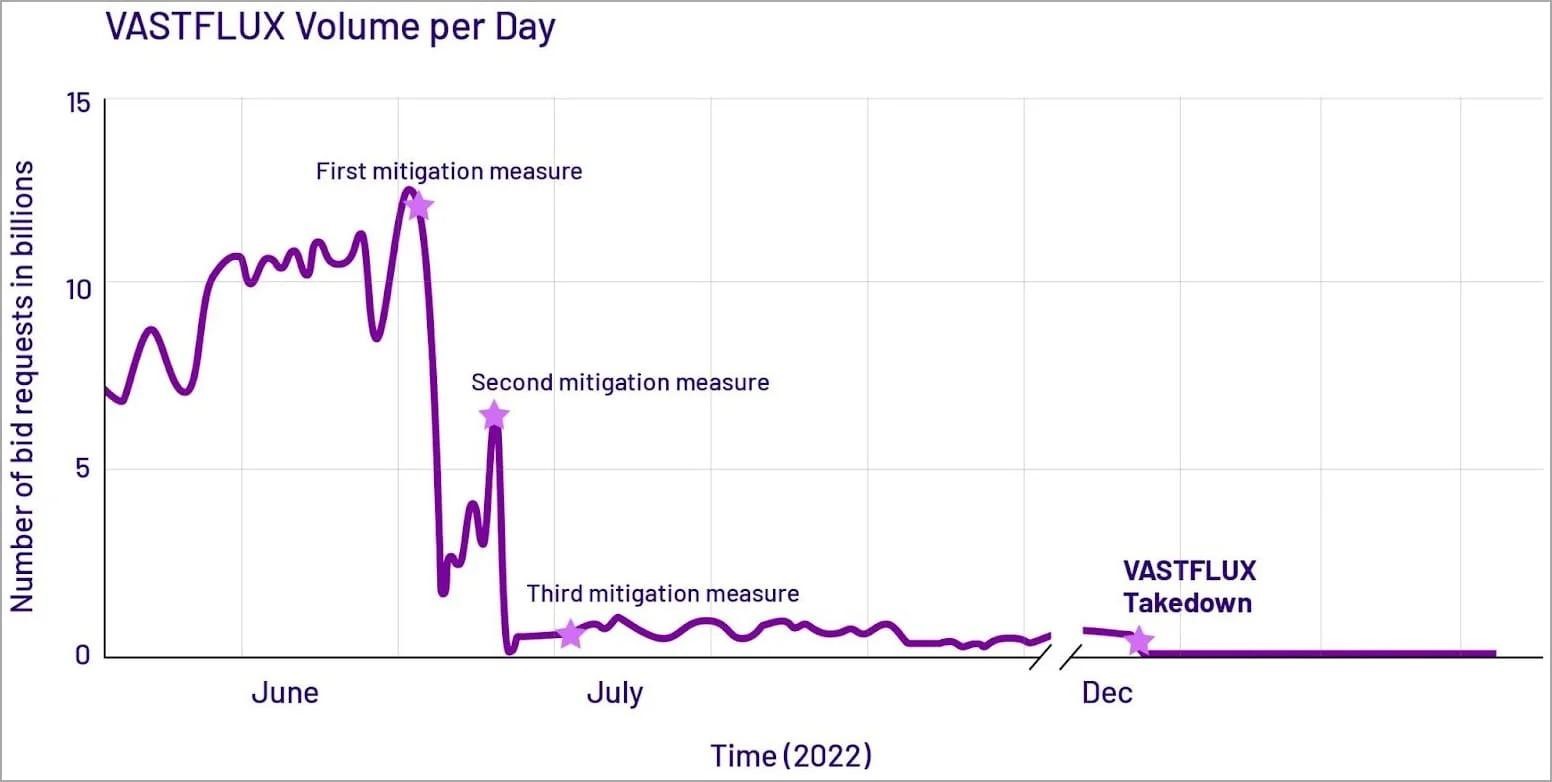
Experts write that after mapping the infrastructure of the Vasstflux operation, in June-July 2022, they launched three waves of “attacks” on fraudsters, supported by a number of clients, partners and fake brands. At first, this forced Vastflux operators to temporarily shut down their C&C servers and significantly reduce the scale of operations, and on December 6, 2022, scam bid requests were reduced to zero for the first time.

Leave a Comment