This article was written to assist users in decrypting Ransomware.
Сryptographer (Ransomware-type infection). Defense against encoders. How to remove the encoder virus? Сryptographers are malicious programs that cipher files and demand ransom for decrypting them. Opinion pieces, instructions for the victims, recommendations for defence and prevention of ransomware-type threats. Digest “Crypto-Ransomware” with the feature of “Hot notification” and “Rapid incident response” applied by Google technologies.
Below we have provided you with several milestones you need to accomplish to restore your data (instead of literally paying the frauds). We definitely urge you not to transfer the ransom amount – if you initiate the payment, you simply sponsor the crooks to elaborate even more sophisticated ransomware samples.
100 % Еffective Solution Against All Ransomware Threats
With the continuously increasing numbers of ransomware threats and their victims, it is obvious that everyone needs to undertake the appropriate precautions against them. The most confident solution to make sure Ransomware can’t damage your data in the future is to back up your data. And the best solution to do that is with the help of cloud storage.
Deletion
Before you start restoring your data you need to make sure that the Ransomware infection itself has been removed. Use the tutorial you were brought from to get rid of it, otherwise it may cipher your data again.
If you can’t delete the ransomware on your own, we recommend you to download Loaris Trojan Remover.
Identification
Below you will find a number of cost-free decryption utilities that can possibly assist you in restoring your data. Nevertheless, you must have the proper tool for the sort of encryption that was applied on your data. To discover that, use ID Ransomware – a cost-free online utility that will inform you what particular ransomware is currently encrypting your data. You’ll be suggested to upload the specific ransom note document (normally discoverable on your desktop), as well as the specimen of the encrypted document.
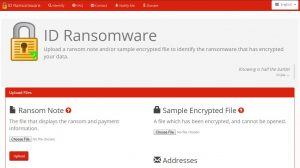
As soon as the analysis is performed, ID Ransomware will notify you exactly which ransomware sort you are combating with.
Decryption
We do not give 100% guarantee that any of these solutions will be effective and they are rendered by their authors as is, but most of the cases they will help you!
For instance, the STOP Djvu ransomware ciphers victim’s files, and adds one of dozens of extensions to filenames; for instance, “.djvu”, “.rumba”, “.radman”, “.gero”, etc.
This ransomware encrypts the data with the help of AES-256 (CFB mode) and, later on, with the help of other algorithms. [Starting from September 2019 the RSA algorithm is actively used]. It’s not the entire file that is ciphered, but about 0x500000 bytes (~5 Mb) at the beginning of each file. Then the ransom is mentioned in the amount of $200-$600 in BTC in order to restore the data. Original name: STOP. The file may contain random data. Development environment: C++ with compilation into MS Visual Studio 2013 (later the newer version of Visual Studio 2017 or the latest one was used).
A company named Emsisoft has elaborated decryptors for most ransomware threats.
Emsisoft stands for a company involved in ransomware decryption and they are very good at that. You can use all decryptors for the ransomware from the range above via their website here. You can obtain your offline keys for your ransomware on the Emisoft website.
Some ransomware-modified files can be successfully restored if they were encrypted by means of an offline key that Emisoft has in place.
For Old Djvu, for instance, files can also be recovered via encrypted/original file pairs uploaded to the STOP Djvu Submission resource.
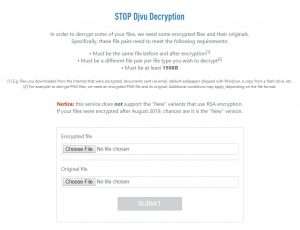
After pressing the SUBMIT button, the service will tell you if the files were properly processed, and if so, will provide a link to the decryptor.

Their decryptors are simple-to-use and there’s nothing hard about applying them. Most decryptor utilities by Emsisoft possess a similar GUI and work in the same manner. Simply start the utility designed for the specific ransomware (no installation is mandatory) and in the resulting window select the folder/disk you’d like to have restored. You can add or uncheck folders with the buttons below. As soon as you’re ready, just choose the folder you need and click on Decrypt.
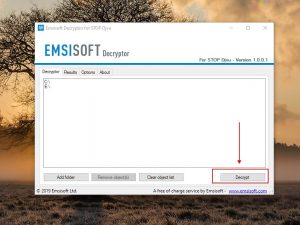
During the decryption process, in case the decryptor has troubles decrypting a certain file type, you should instruct the service by means of uploading encrypted and non-encrypted pairs of such files. As soon as this is completed, you should repeat clicking on the Decrypt button in order to make it process this specific file type.
Waiting for a solution
Neither ransomware threats nor their authors are immune or ideal and the above-said range of decryptors is the good evidence of that. Sadly, it normally takes time for security researchers to break into the ransomware code and come up with the solution we really should have in place. Even if there is no decryptor utility in place now this doesn’t mean one won’t be revealed in the future. If you have found any other working ransomware removal solution or file restoration method in place, feel free to share it with us.

Leave a Comment