Cloudflare representatives said that some employees of their company were attacked by hackers using phishing SMS, and their credentials were stolen. Twilio employees were subjected to a similar attack last week, and the company was eventually hacked.
Let me remind you that earlier this week it became known about the hacking of Twilio, a company engaged in the development and provision of cloud PaaS services. It turned out that in early August, unknown attackers gained access to the data of some of her clients, having previously compromised the accounts of Twilio employees.
As part of a phishing attack on Twilio employees, hackers posed as representatives of the company’s IT department. In their SMS messages, they asked people to click on links containing keywords such as Twilio, Okta and SSO, after which the victims were taken to a fake Twilio login page. People were persuaded to click on malicious links with warnings that their passwords had supposedly expired or that it was time to change them according to the plan, as they were out of date.
Twilio officials wrote that other companies were subjected to similar attacks, together with which Twilio tried to leave the attack of intruders. The names of other affected companies were not disclosed.
As Cloudflare now reports, one of the targets of the hackers was its employees. In dit geval, the attackers carried out the same phishing attack via SMS and successfully stole the credentials, but were unable to log in with them: the hackers did not have access to the FIDO2 keys that the company uses.
A total of 76 employees and their families received phishing messages. The fakes originated from T-Mobile numbers and redirected victims to fake Cloudflare Okta login pages hosted on the cloudflare-okta[.]com domain. This domain was registered through the Porkbun registrar, which was also used to register the domains seen in the Twilio attack.
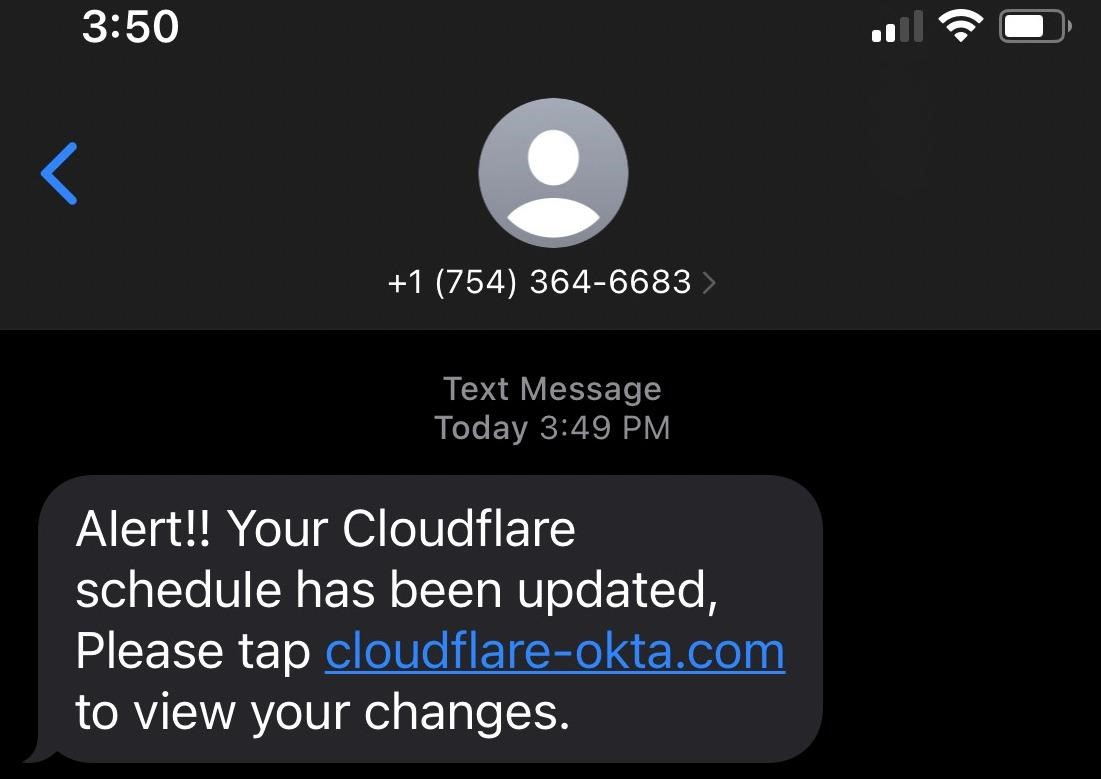
Although the attackers tried to enter our systems with compromised credentials, they were unable to bypass the hardware key requirement.the company says.
Cloudflare reportedly took a number of protective measures following the attack:
- blocked a phishing domain using Cloudflare Gateway;
- identified all affected Cloudflare employees and reset compromised credentials;
- identified and blocked the infrastructure of intruders;
- updated detection methods to identify any subsequent attack attempts;
- audited access logs looking for additional signs of attacks.

Laat een reactie achter