According to experts at e-commerce security company Sansec, at least seven hacker groups are behind the massive TrojanOrders attacks that have recently affected Magento 2-based sites.
Such attacks use the critical vulnerability CVE-2022-24086, discovered and fixed at the beginning of the year, affecting 어도비 벽돌 Commerce and Magento.
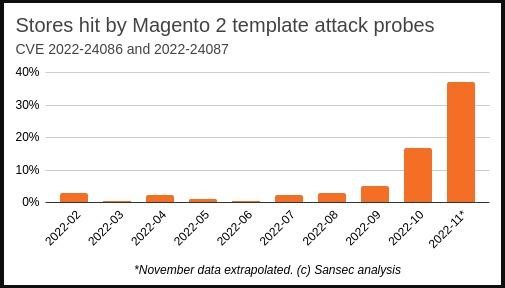
Number of attacked sites is rising
우리도 그렇게 썼다는 것을 상기시켜 드리겠습니다. E-Commerce Software Developer FishPig Hacked in a Massive Supply Chain Attack, 그리고 그것도 Operators of the Clipminer Botnet “Earned” More Than $1.7 백만.
Let me remind you that the CVE-2022-24086 취약성 (9.8 points out of 10 on the CVSS scale) was discovered and fixed in February 2022. The bug allowed remote arbitrary code execution without authentication. According to Adobe, the root of the problem was incorrect input validation.
From the very beginning, it was reported that hackers had already begun to exploit the problem. Later, such attacks on CVE-2022-24086 were given the name TrojanOrders (“Trojan Orders”), as attackers get the opportunity to execute code and inject RAT (remote access trojans) on uncorrected store sites.
일반적으로, when carrying out TrojanOrders attacks, hackers create an account on the target site and place an order that contains malicious code in one of the fields.
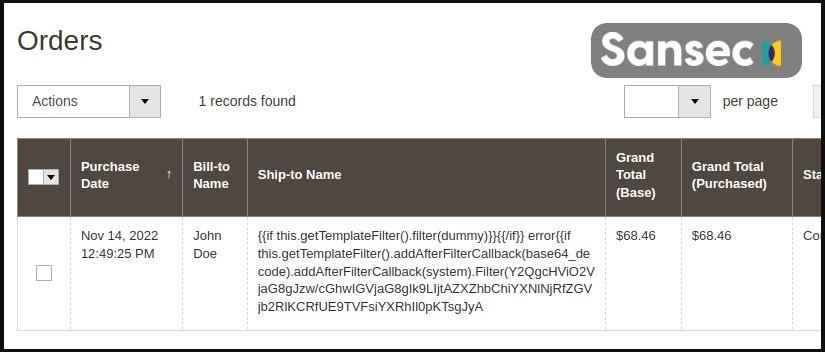
예를 들어, the attack on the screenshot above will inject a copy of the health_check.php file into the site, which contains a PHP backdoor that can run commands sent via POST requests. Once they gain a foothold on a site, attackers implement RATs to ensure they have constant access and the ability to perform more complex actions.
동시에, in many cases studied by Sansec, immediately after the compromise, the hackers searched the site for the health_check.php file to determine if another group had previously infected the resource. If the answer was positive, the attackers would replace this file with their own backdoor.
Ultimately, the attackers modify the site’s code by injecting malicious JavaScript into it, which steals information about customers and their bank card numbers.
Unfortunately, according to Sansec analysts, the administrators of many sites have not yet installed the necessary patches, and the vulnerability still poses a significant threat. Researchers say that almost 40% of Magento 2 sites are attacked, with hack groups literally fighting each other for control of infected resources.
Such attacks can lead to serious failures in the operation of sites and the massive theft of bank cards of buyers, especially amid of the upcoming Black Friday and Cyber Monday.
Worse, the researchers believe that this trend will continue as we approach Christmas and New Year. The fact is that PoC exploits for this problem have been available for a long time and are included in many exploit kits, the number of unpatched sites is still high, and the holiday sales season is coming.
It is noted that exploits have become so numerous that they are sold for as little as $2,500, while at the beginning of 2022 they cost from $20,000 에게 $30,000.
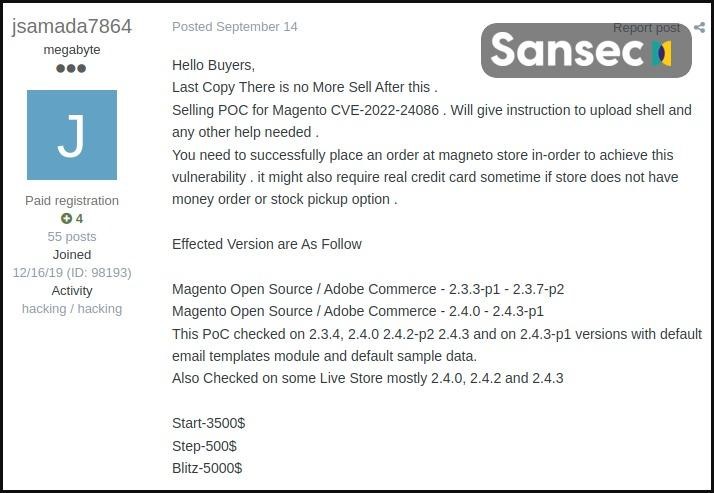
Exploit Sale

코멘트를 남겨주세요