ESET analysts have noticed that the Chinese hack group Evasive Panda has hacked into the Tencent app and attacked an unnamed international non-governmental organization (NGO) operating in China.
The attack was carried out using the MgBot malware, which was made part of an automatic update for the Tencent QQ messenger.
Let me remind you that we also wrote that Chinese Government Hackers Successfully Spy on Organizations in Europe, Australia and Southeast Asia, and also that Two Hack Groups at Once Hacked into a Federal Agency in the United States Using a Four-Year-Old Bug. And also the media wrote that Chinese Cybercriminals Stole over $500 million from Indians.
Evasive Panda, also known as Bronze Highland and Daggerfly, is a Chinese APT group that has been linked since 2012 to cyber-espionage attacks targeting various targets in China, Hong Kong and other countries located in East and South Asia.
One of the distinguishing features of the grouping is the use of the MgBot modular framework, which is able to receive additional components on the fly to expand its information collection capabilities. So, among the capabilities of this malware written in C ++, there are file theft, keylogging, data theft from the clipboard, audio recording and theft of credentials from browsers.
At the same time, most MgBot plugins are designed to steal information from popular Chinese applications, including QQ, WeChat, QQBrowser and Foxmail, developed by Tencent.
ESET says it discovered the Evasive Panda malware campaign in January 2022, when a legitimate Chinese app was used to deploy the MgBot backdoor installer. According to the company, the targets of the hackers were in the provinces of Gansu, Guangdong and Jiangsu and were members of an unnamed international non-governmental organization. Interestingly, the MgBot backdoor installer appears to have been discovered and removed while it was being downloaded to the victims’ computers, and attempts to compromise were unsuccessful.
According to the researchers, the MgBot malicious payload was delivered to victims as an update for Tencent QQ from legitimate URLs and IP addresses belonging to the developers of this software. Effectively, this means that either a supply chain attack or an adversary-in-the-middle attack has occurred.
In the first case, Evasive Panda would have had to hack into Tencent QQ’s update servers in order to infect the QQUrlMgr.exe file with malware, which was then delivered to the victims under the guise of a legitimate update.
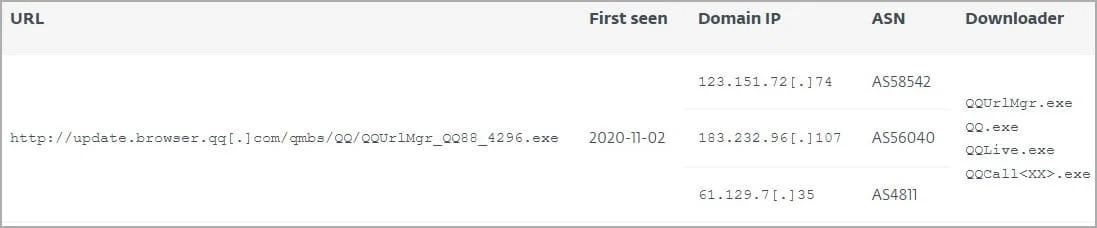
The researchers note that malicious versions of the update file downloaded the malware itself from a hard-coded URL (update.browser.qq[.]com) and used a hard-coded decryption key that matched the correct MD5 hash provided by the server. However, the legitimacy of this URL has not yet been confirmed, and Tencent representatives did not answer the question of ESET. In addition, analysts were unable to obtain a sample of the XML data from the server, which would have provided a better understanding of the malware delivery mechanism.
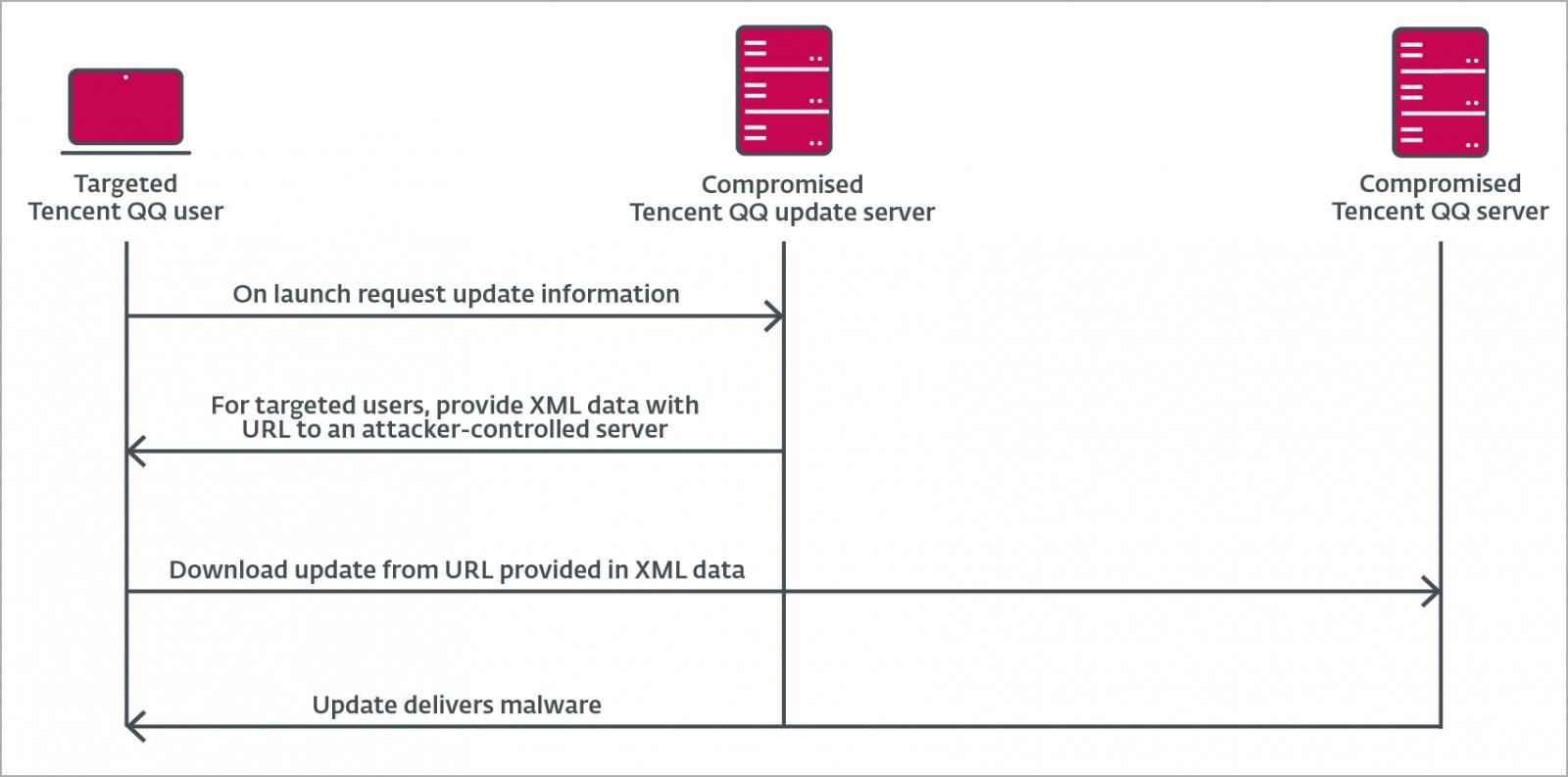
Possible attack pattern
As for the second scenario, adversary-in-the-middle attacks, the researchers noticed similarities with other malware campaigns that used this tactic, including one of the LuoYu APT attacks.
During that campaign, the WinDealer malware was used, which generated random China Telecom IP addresses to perform AITM attacks. These IP addresses appeared to be in the same ranges as the ones that the MgBot delivered in the Evasive Panda campaign.
In addition, attackers could compromise vulnerable devices such as routers or gateways and use them to attack.

Leave a Comment