Chinese government hackers have been conducting a months-long cyber-espionage campaign against entities in Australia, Malaysia and Europe, as well as companies operating in the South China Sea.
The campaign targets Australian government agencies, Australian media and global heavy industry companies that maintain wind turbines in the South China Sea. In a joint report, Proofpoint and PwC attributed the espionage to APT40 (Leviathan, TA423, Red Ladon). In addition, the Ministry of State Security of China (MGB PRC) is allegedly behind the activities of APT40.
Let me remind you that we also wrote that Trojan Woody Rat attacks Russian Organizations, and also that Media said that BMW and Hyundai have been hacked by Ocean Lotus.
Several waves of phishing campaigns were carried out between April 12 and June 15 and used initiating URLs from Australian media companies to deliver the ScanBox intelligence tool. The phishing emails contained topics such as “Sick Leave”, “User Research”, and “Cooperation Request”.
In the attack, the hacker posed as an employee of a fictitious Australian media outlet and provided a malicious domain URL, urging the victim to browse a website or share research content for publication on the site. APT40 uses a controlled domain that is used to deliver malware.
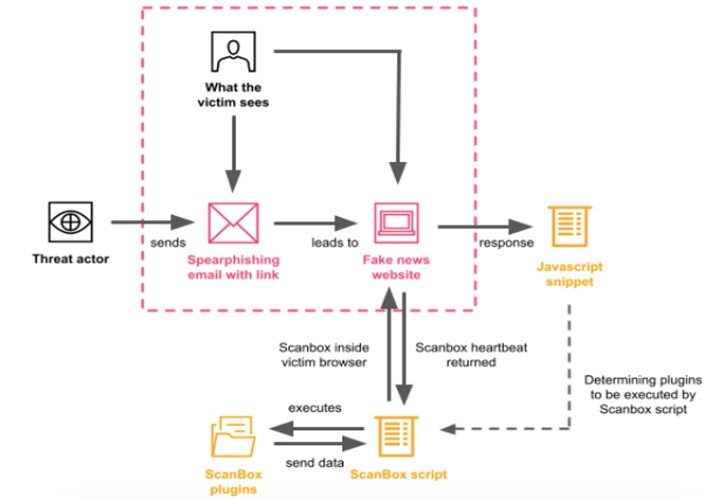
ScanBox is JavaScript-based malware that allows a hacker to profile its victims and deliver a next-stage payload containing the HUI Loader, PlugX, and ShadowPad RAT trojans.
ScanBox extracts and launches several plugins in the victim’s web browser that:
- register keystrokes;
- remove the fingerprint of the browser;
- collect a list of installed browser add-ons;
- exchange data with infected machines;
- check for the presence of Kaspersky Internet Security (KIS).
Also, these attacks used malicious RTF documents to deliver a first stage loader, which then acted as a conduit to obtain encoded versions of the Meterpreter shellcode. One of the victims of this campaign in March 2022 was a European manufacturer of heavy industrial equipment for offshore wind farms in the Taiwan Strait.
Scanbox is already known to the cybersecurity community. It was used by Chinese cyber spies from APT 10 as part of a campaign against members of the US National Foreign Trade Council.
Also in 2019, unknown attackers compromised a Pakistani government website and infected it with a keylogger and other malware to collect data from users checking the status of their application for Pakistani citizenship.

Leave a Comment