At the beginning of this year, Avast experts released a free decryptor for files affected by BianLian ransomware attacks, and after that, ransomware operators changed tactics and no longer encrypt the data of their victims. Now they simply steal information from compromised networks and use it for extortion, forcing victims to pay for silence.
Let me remind you that we also wrote that Los Angeles Unified School District Hit by Ransomware Attack, and also that Two Hack Groups at Once Hacked into a Federal Agency in the United States Using a Four-Year-Old Bug.
The BianLian ransomware was first spotted by security experts back in July 2022 after it successfully hacked several well-known organizations. In January 2023, Avast released a free decryptor that helps victims recover their files affected by malware attacks.
Avast specialists are generally intricate guys, for example, the media wrote that Avast expert taught Smarter Coffee machine to ransom money.
As Redacted researchers now report, after the advent of the decryptor, malware operators were forced to change their approach to attacks.
The specialists write that in general, BianLian uses the same methods to gain initial access and lateral movement in the networks of victims, and also continues to deploy its own Go-based backdoor on infected systems, which provides remote access to a compromised device.
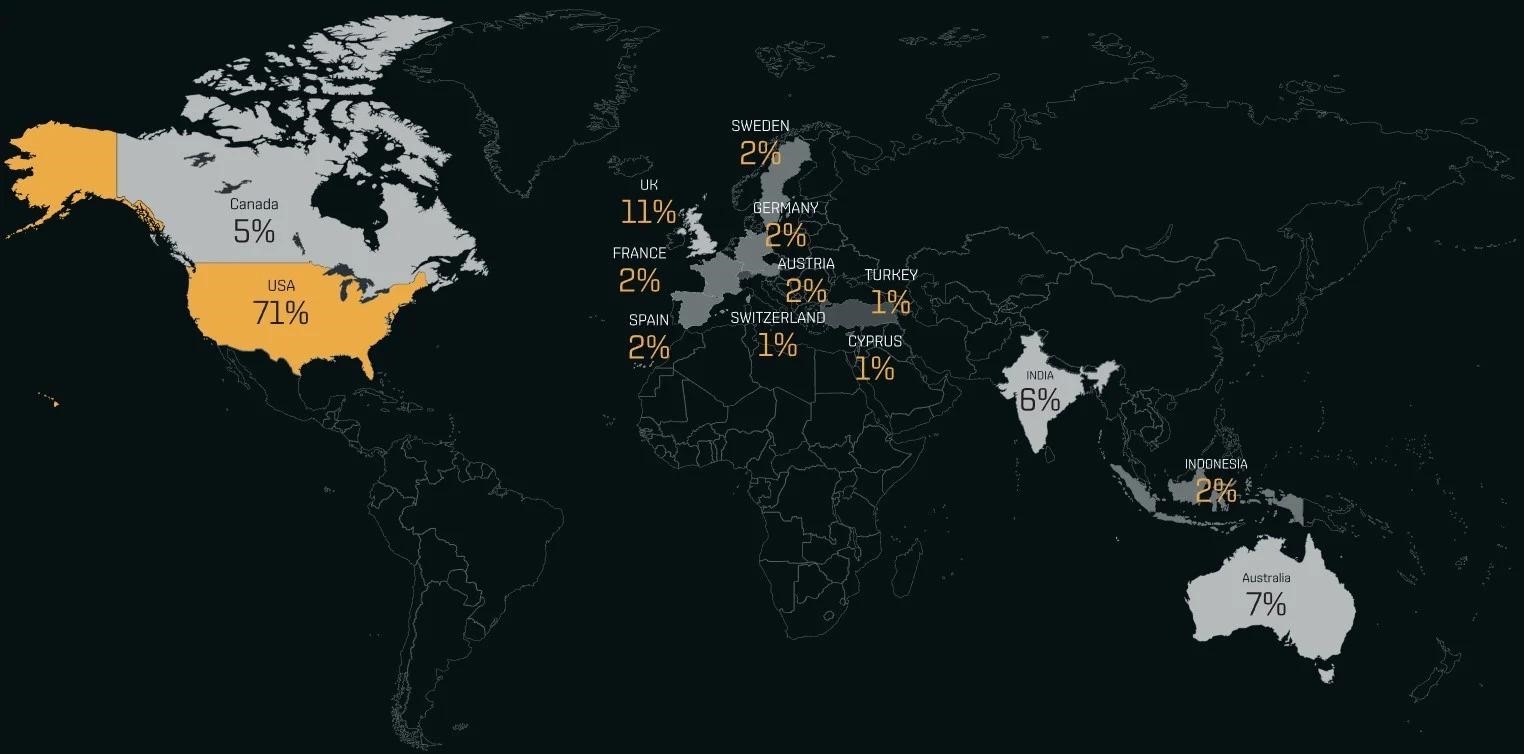
48 hours after the hack, the hackers are already posting veiled information about the victims on their website, giving them about 10 days to pay the ransom. As of March 13, 2023, BianLian operators have listed 118 entities on their website, with the vast majority (71%) being US-based companies.
The main difference in the group’s recent attacks has been attempts to monetize hacks without file encryption. Now hackers rely solely on threats and promise to “leak” stolen data if they are not paid.
It is also noted that the hackers are clearly conducting their own research and adapting messages for specific victims in order to increase pressure on the victims. For example, in some cases, attackers threaten victims with the legal and regulatory challenges they will face if their data is “leaked” to the public. At the same time, the laws cited by the hackers are quite consistent with the jurisdiction in which the victim company is located.
It is not known whether the Avast decryptor was the reason for the refusal of encryption, or whether its release only helped hackers understand that they do not need this part of the attacks to extort ransoms from victims.
It must be said that BianLian is not the only group that engages in extortion without encryption. The now defunct Babuk and SnapMC have gone down this path before, and there is ransomware that claim not to be directly involved in file encryption, including RansomHouse, Donut and Karakurt.
However, most hack groups continue to use encryption in their attacks, as disruptions to companies caused by such malware usually put enormous pressure on those affected.

Leave a Comment