Dropbox reported that in mid-September, its employees were attacked by hackers that penetrated into their GitHub accounts.
Using phishing, the attackers managed to gain access to one of the company’s GitHub organizations, and then stole data from 130 repositories.
You might also want to know About 1,900 Signal Accounts May Be Compromised Due to the Twilio Hack.
The incident occurred on October 14, 2022, and was associated with a large-scale phishing campaign, which GitHub representatives had previously warned about. Let me remind you that as part of this scheme, scammers sent letters with fake notifications on behalf of the Circle CI service, which is used for continuous development and deployment.
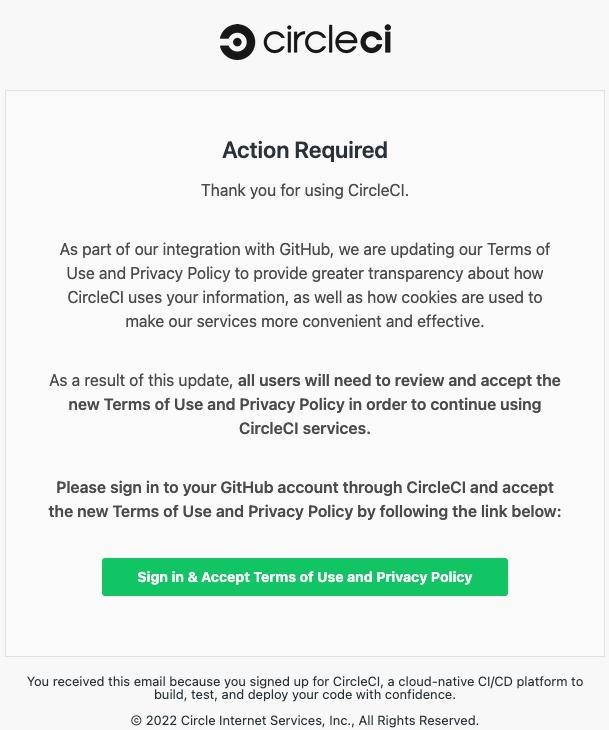
Example of a phishing message
These emails, for example, notified recipients of changes in the privacy policy and terms of use, ostensibly requiring people to sign in to their GitHub account and accept the changes. As you might guess, the goal of the attackers was collection of credentials from GitHub and two-factor authentication with one-time passwords (OTP), which were transmitted to the attackers through reverse proxies.
Dropbox reports that one of the employees of the company fell for the trick from such an email that looked exactly like the real thing. As a result, the attackers gained access to one of the company’s GitHub accounts.
Company representatives write that having gained access to one of the company’s GitHub accounts, the attackers managed to infiltrate one of the Dropbox GitHub organizations, from where they eventually copied 130 repositories.
These repositories contained “copies of third-party libraries slightly modified for Dropbox use, internal prototypes, a number of tools, and configuration files used by the security team.” It is emphasized that the repositories did not contain the code of the main applications or infrastructure, and access to such repositories is limited and strictly controlled.
Immediately after the detection of suspicious activity, attackers’ access to GitHub was disabled. Dropbox security experts updated all compromised developer credentials and determined which customer data was exposed or stolen. The company is currently working on a WebAuthn rollout that was in progress prior to the incident and will now be accelerated.

Leave a Comment