The New Zealand company Mega, which develops the file sharing service of the same name, has eliminated a number of serious vulnerabilities that led to the disclosure of user data, even if they were stored in encrypted form.
Let me remind you that we also wrote that Vulnerability in WhatsApp could remotely compromise a user’s device.
One of the main features of Mega, which the company focuses on in advertising, is end-to-end encryption, where only the user has access to the decryption key.
However, researchers from the ETH Zurich demonstrated that vulnerabilities in the encryption algorithm allowed access to encrypted user data, which could, among other things, be used by employees of Mega or the organization that controls the file hosting infrastructure.
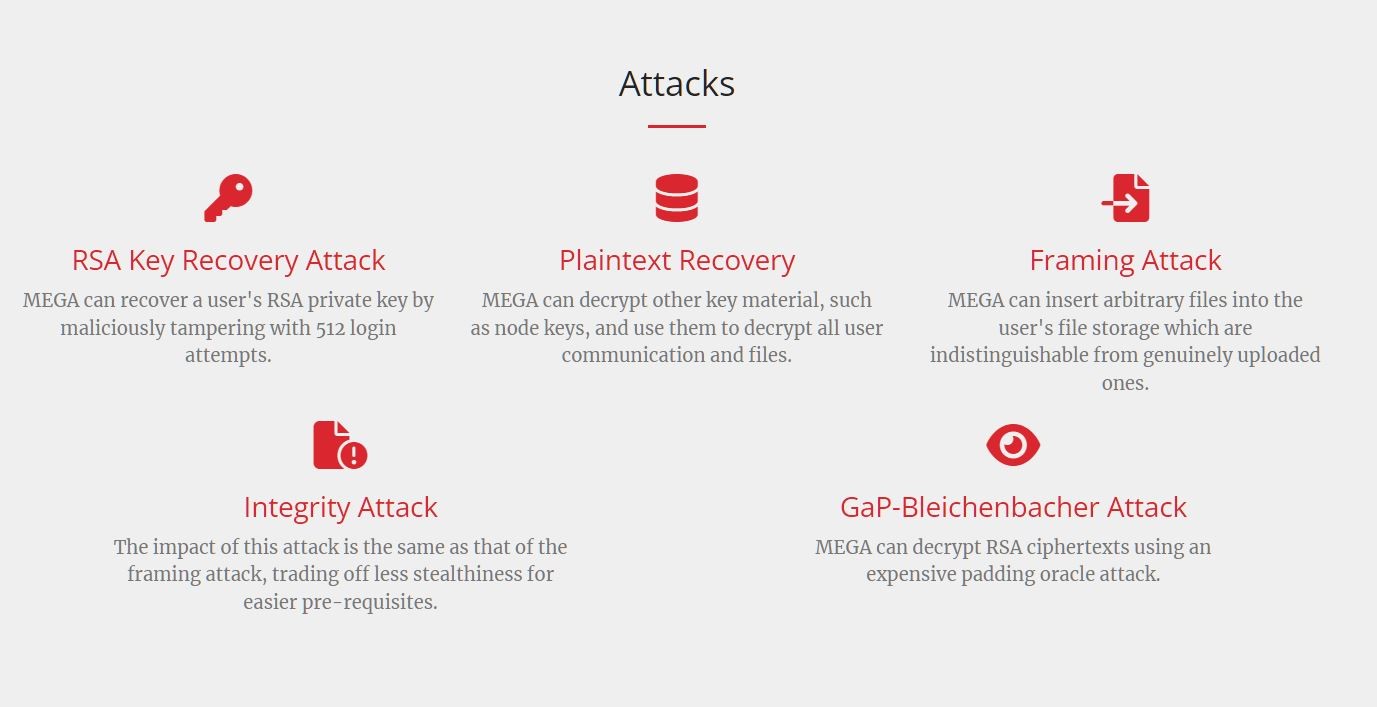
Encryption vulnerabilities were discovered in March 2022. Although the researchers found five possible attack vectors against user data, they all rely on the theft and decryption of the RSA key.
The expert report states that Mega uses a user-controlled end-to-end encryption (UCE) system to protect data even from internal access. The basis of this system is an encryption key generated from the user’s password, which he uses to log into the system.
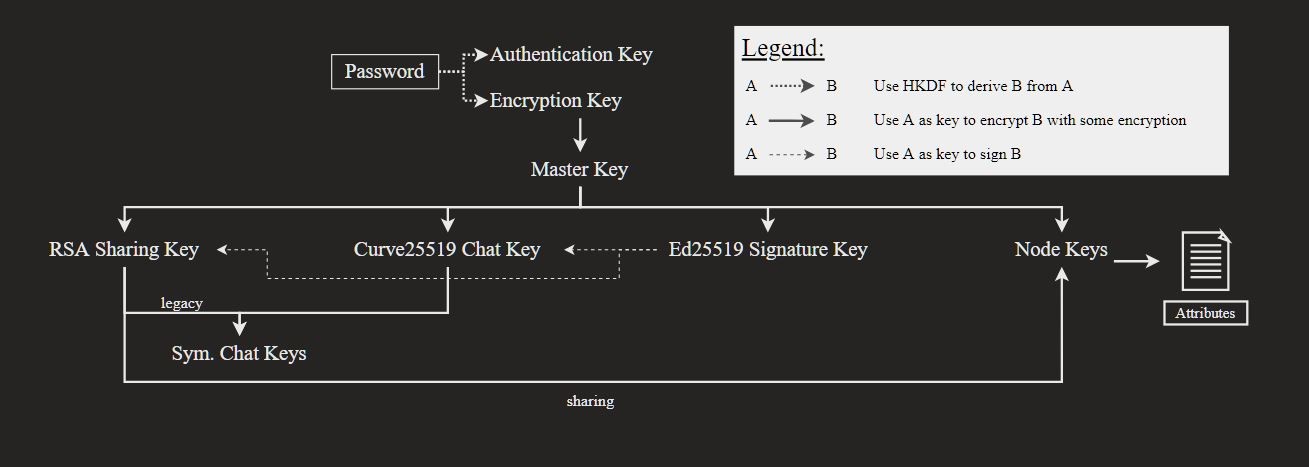
A master key is then generated using a randomized process and used to subsequently encrypt a subset of keys, including the RSA key pair, the Curve key used for chat, and the Ed signing key and Node keys.
The fact is that the user’s RSA key is stored on Mega servers without integrity protection, and the researchers came up with a new way to perform a man-in-the-middle attack that allows you to recover RSA keys for target accounts.
This attack is based on guessing the prime factor by comparison and will require at least 512 login attempts to work. Moreover, the attack also requires access to the Mega servers. Of course, getting access to the servers is very difficult from the outside, but not so difficult for possible insiders, for example, working in Mega itself.
Once the RSA key for the target account is leaked, the attacker is able to recover the AES-ECB master key and then decrypt the entire subset of keys. As a result, the hacker will be able to decrypt user data stored in the Mega cloud, access chats, and even upload new content to the compromised account’s storage.
As a result, Mega developers, to whom experts reported their findings back in the spring, fixed three vulnerabilities that could lead to decryption of user data on all clients, and also plan to fix the remaining two problems in the next updates.
The company also emphasized that they did not find any signs of illegal access to user accounts and data, both from insiders and from outside.

Leave a Comment