This article intends to help you delete Redl Ransomware for free. Our guidelines also explain how any .redl files can be restored.
About Redl
Redl Ransomware stands for a cryptovirology PC danger made use of to blackmail its targets. Redl Virus may not indicate any type of evident signs and symptoms, yet its existence is just found as quickly as its task is carried out.
The absence of signs and symptoms is one of the main problems with this type of PC infections. They can pass through into the assaulted system undetected, as well as execute their job without revealing their activity in the workstation. This is why most customers are unable to do anything to terminate the virus prior to it has actually finished its goal, and the objective of this one, specifically, is to make its targets' files unusable by means of data ciphering and after that showing a ransom demand.
The user is reported by means of a message that this infection places on their display that their only solution of bringing their data back is by means of the payment of a particular amount of funds. This blackmailing part of this rip-off is incredibly popular among the fraudulences, and also there's a whole team of COMPUTER malware that's made use of in this way. This malware group is called Ransomware, and also the malware we are currently concentrating on absolutely drops under it.
The Redl malware is only disclosed once it has completed encrypting the documents. The .redl Ransomware will certainly then express its demands using an challenging pop-up alert.It is through this alert that the individuals discover how they are expected to transfer their funds to the cyber frauds in charge of the Ransomware infection. In the majority of instances, the ransom would certainly be asked in a cryptocurrency - BitCoin. These cryptocurrencies are actually difficult to trace, as well as a regular user would have no chance of recognizing that they are truly transferring their funds to. This, actually, makes it actually not likely that the cyberpunk's true identity would certainly ever before obtain divulged. It is fairly uncommon for a Ransomware cyberpunk to stand before the court, and the application of cryptocurrency as the suggested payment solution is the major reason for that.
Below you can find the quote from the Redl text file:
ATTENTION! Don't worry, you can return all your files! All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key. The only method of recovering files is to purchase decrypt tool and unique key for you. This software will decrypt all your encrypted files. What guarantees you have? You can send one of your encrypted file from your PC and we decrypt it for free. But we can decrypt only 1 file for free. File must not contain valuable information. You can get and look video overview decrypt tool: https://we.tl/t-2P5WrE5b9f Price of private key and decrypt software is $980. Discount 50% available if you contact us first 72 hours, that's price for you is $490. Please note that you'll never restore your data without payment. Check your e-mail "Spam" or "Junk" folder if you don't get answer more than 6 hours. To get this software you need write on our e-mail: restorealldata@firemail.cc Reserve e-mail address to contact us: gorentos@bitmessage.ch Our Telegram account: @datarestore
How to Redl virus encrypt your files?
The .redl Infection file security is not going to be gotten rid of after the ransomware is removed. The .redl Virus document encryption access key is promised to be given to you when you pay the ransom amount.
However, it is not uncommon for the criminals that guarantee such risks to assure their sufferers a decryption key for their encrypted files only to reject to provide that essential as soon as the settlement obtains processed. Needless to mention, if you end up in a condition similar to this, you wouldn't can doing anything regarding it-- your funds would certainly be gone, and your data would still be hard to reach. This is why it isn't really sensible idea to transfer the repayment, in addition, if you haven't gone with any kind of alternate choices that may be effective.
Although we pointed out that the security would certainly continue to be on your documents also after the Ransomware is no more in the system, removing the infection is still extremely important. After you eliminate the Ransomware, you may also attempt the different documents healing options we have actually established for you, as well as additionally your new documents will not go to risk of being secured. To delete this cryptoviral hazard, you are recommended to complete the actions you will certainly run into below.
Redl SUMMARY:
| Name | .redl Virus |
| Type | Ransomware |
| Threat Level | High (Ransomware is up until now the most awful malware you can experience) |
| Symptoms | A Ransomware threat like this one would typically not expose its visibility up until the files obtain secured |
| Promotion Channel | Channels like spam e-mail promotion, and malvertising are normally the ones used to spread Ransomware. |
| Data Recovery Solution | Emsisoft Decrypter |
| Detection Utility |
.redl may recover itself plenty of times if you don't get rid of its core files. We suggest downloading Loaris Trojan Remover to scan for malicious utilities. This may save you a lot of time and efforts to effectively get rid of all possible malware within your device.
Read more about Loaris Trojan Remover (License Agreement, Privacy Policy ).
If Loaris identifies a threat, you will need to buy a license to get rid of it. |
Delete Redl Virus Ransomware
Some of the steps will likely demand you to exit the page. Bookmark it to easily get back to it later.
Reboot in Safe Mode (use this tutorial if you don’t know how to do it).
Click CTRL + SHIFT + ESC simultaneously and go to the Processes Tab. Try to identify which processes are malicious.
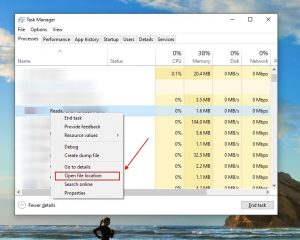
Right click on each of them and choose Open File Location. Then inspect the documents with online file checker:
Once you open their folder, end the processes that are contaminated, then get rid of their folders.
Note:If you are certain something is part of the threat - remove it, even if the scanner doesn't mark it. No anti-virus application can determine all infections.
Keep holding the Win + R. And then copy & paste the following:
- notepad %windir%/system32/Drivers/etc/hosts
A new document will open. In case you are hacked, there will be a tons of various other IPs connected to your device at the bottom. Examine the image below:
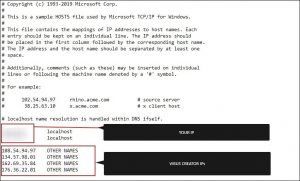
In case there are suspicious IPs below “localhost” – get in touch with us in the comments.
Use CTRL + SHIFT + ESC simultaneously and access the Startup Tab:
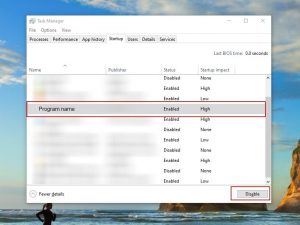
Proceed to Program Name and select “Disable”.
Keep in mind that ransomware may even include a fake developer name to its process. You must check out every process and be persuaded that it is legitimate.
To get rid of Redl Virus, you may have to deal with system files and registries. Making a mistake and getting rid of the wrong thing may hurt your device.

You can prevent the system damage by selecting Loaris Trojan Remover - a high-quality Redl removal software.
Read review about Loaris Trojan Remover (License Agreement, Privacy Policy ).
Look for the ransomware in your registries and get rid of the entries. Be very careful – you can destroy your system if you remove entries not associated with the ransomware.
Type each of the following in the Windows Search Field:
- %AppData%
- %LocalAppData%
- %ProgramData%
- %WinDir%
- %Temp%
Get rid of everything in Temp. Finally, simply check out for anything lately added. Don't forget to drop us a comment if you run into any issue!
How to Decrypt .redl files?
Djvu Ransomware essentially has two versions.
- Old Version: Most older extensions (from “.djvu” up to “.carote”) decryption for most of these versions was previously supported by STOPDecrypter tool in case if infected files with an offline key. That same support has been incorporated into the new Emsisoft Decryptor for these old Djvu variants. The decrypter will only decode your files without submitting file pairs if you have an OFFLINE KEY.
- New Version: The newest extensions released around the end of August 2019 after the ransomware was changed. This includes .coharos, .shariz, .gero, .hese, .xoza, .seto, peta, .moka, .meds, .kvag, .domm, .karl, .nesa, .boot and etc….These new versions were supported only with Emsisoft Decryptor.
"The decrypter can't decrypt my files?"
For the most part this indicates you have an online ID. It can additionally indicate your files were secured by a more recent version of STOP/Djvu.
- Offline ID. When the ransomware can't connect to its command and control web servers while encrypting your files, it utilizes a built-in security key as well as a built-in ID. Offline ID's usually end in t1 and also are normally easy to determine. Given that the offline key as well as ID only transform with each variant/extension, every person who has actually had their documents encrypted by the exact same version will certainly have the same ID as well as the files will be decryptable by the very same key (or "private key in the case of RSA file encryption).
- Online ID. In many cases the ransomware is able to attach to its command and control servers when it secures files, and also when this occurs the servers respond by creating arbitrary keys for each and every contaminated computer system. Since each computer system has its own key, you can not use a key from one more computer to decrypt your documents. The decrypter can functioning about this with older variants as long as it has some help, however for newer variants there is absolutely nothing that can be done to recuperate data.
In case when the tutorial doesn’t help, download the anti-malware tool we suggest or try free online virus checker. Furthermore, you may always ask us in the comments for assistance!

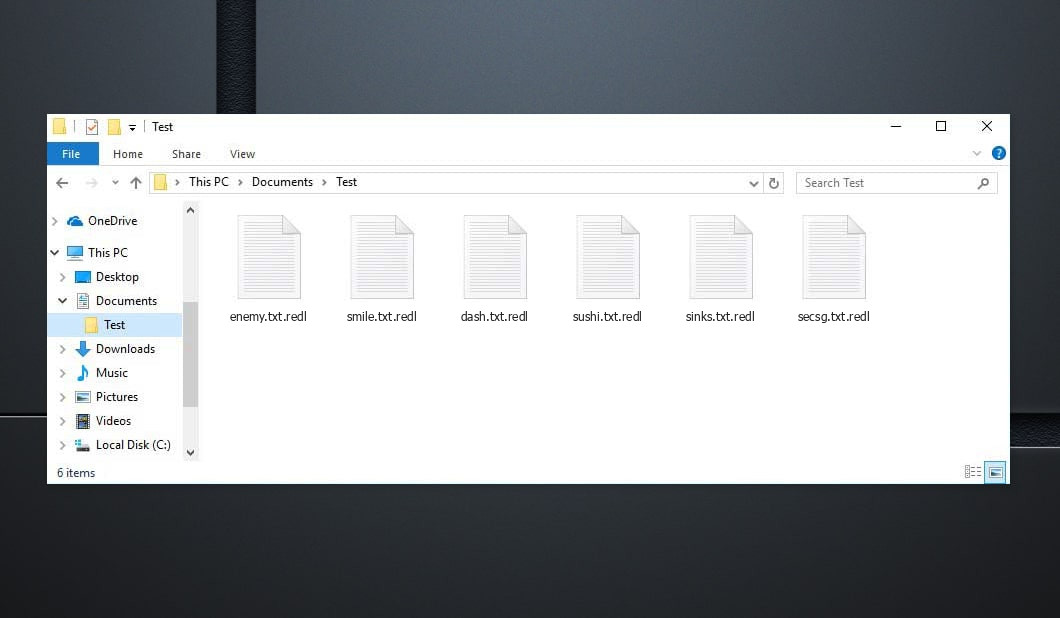
This My Result, i dont remove this variant helpme and tools save my files descripter,…. Gracias
Result:
We have identified “STOP (Djvu)”. This ransomware may be decryptable under certain circumstances.
Please refer to the appropriate guide for more information.
Identified by:
ransomnote_email: helpmanager@iran.ir
sample_extension: .redl
sample_bytes: [0x3F2C – 0x3F52] 0x7B33364136393842392D443637432D344530372D424538322D3045433542313442344446357D
Click here for more information about STOP (Djvu).
Case number: 91af91e800c2ff5a4cb16d85069abbecc4843d461579188076