Best Defense Against Ransomware: Maintaining your data duly protected against ransomware is crucial today. The viruses belonging to the ransomware family can damage the essential documents or photos of your family that you cherish the most. Furthermore, these threats are actively distributed on the web through tricky methods. The main reason why their distribution rates grow by leaps and bounds is that they generate massive revenue for online fraud. Regretfully, many victims have decided to eventually pay the ransom into the pockets of cyber crooks and thus wasted their money for nothing. Therefore, there is a great demand for proper protection against ransomware threats in all their variety.
What is ransomware in the first place?
Ransomware stands for a computer virus that encrypts the data on the infected computer and asks the user to transfer the ransom to regain access to the files. Most ransomware-type threats use AES or RSA encryption mechanisms to cipher the data securely. Regretfully, there is no other option to revert the encryption process without the unique key. Once the encryption is accomplished, the secret key is generated. If bought by the victim, it is supposed to be transferred to the authors of the ransomware to restore the data. However, as mentioned above, there is no guarantee that the crooks will keep their promises.
Another peculiarity of ransomware is that it appends a specific file extension to all the data it modifies. The fact that the extension was added means that the particular document was modified by certain ransomware. Furthermore, a special ransom note is dropped into the folder containing the encrypted data with information about the ransom amount and the payment instructions. Finally, the malware authors instruct the users to transfer the payment using the cryptocurrency according to the specified crypto-wallet destination within a certain period.
Ransomware developers also threaten the victims that their files will be encrypted forever or that the data will be deleted if the computer owners fail to pay the ransom amount. Of course, we all have important documents that we cherish, so losing important information is a tragedy. Hence, we all understand how important it is to protect our valuable information against the aforementioned ransomware-type infections.
Tips to prevent ransomware infiltration.
We must admit that there is no guarantee that the ransomware attack will always be prevented. Hackers invent new tricks daily to inject malicious codes eventually. However, you must adhere to certain principles to protect your device.
We have prepared some valuable recommendations for you to follow. They will help you understand the main principles of maintaining your device secure and the data always available.
Don’t forget about regular data backups.
The best way to protect your information is to make backups of it. Nevertheless, some people ignore this advice or do not perform the backups as often as they should. It may be too late someday, especially when it comes to ransomware.
Hence, the availability of proper backup is of crucial importance. Simply ensure all your important data is properly stored, or standalone storage is not connected regularly to your main device. This can be a USB, CD, or hard drive. Some ransomware threats may also infect the files stored on cloud storage. Therefore, it might not be the best solution.
Make sure your software is up-to-date.
You must have your operating system duly updated against all possible security leakages. When the software is out-of-date, the risk of infection penetration increases essentially. Make sure you install the updates regularly. When you use Windows 7 or higher versions, the automatic update is available, so make sure this option is enabled.
Malware developers and distributors often use various bugs in the software, which makes the software more vulnerable. The frauds always know when the specific system has outdated software. Therefore, they may easily attack such devices and eventually reach their malicious objectives.
Exercise personal caution while online.
You have to realize how important your role is in securing your system. This is especially true when you browse the web. Indeed, you have to be very picky when selecting the sites to visit. Make sure you visit only reliable resources. Consider reading the reviews about specific websites online, for example, the information on the VirusTotal database regarding certain domain names you attempt to visit.
Another important recommendation is to be careful on popular networks or through your email provider. Do not click on suspicious links with tricky instructions. The ransomware is often spread through dubious links that may contain deceptive statements. Stay away from opening suspicious attachments from unknown addresses.
Last but not least, make sure you always use strong and reliable passwords for your accounts. Depending on your preferences, this includes your Google account, social networks, and other popular Internet accounts. It is a good idea to periodically change your passwords instead of using the same passwords for all accounts for several years.
Consider installing reliable security software.
We must regretfully admit that many anti-virus programs today claim to be effective in defending your device. However, they often prove to be ineffective. You may have heard about popular security applications or even use some of such products. In contrast, the ransomware attacking your computer means that the software simply failed to provide its direct function.
If this is so, we recommend you immediately reconsider your choices and switch to the software that can perform the advertised function much better. Loaris Trojan Remover is an excellent utility with an anti-ransomware feature integrated into the main functionality. It will perform its brilliant work regularly, whereas its power to defend the system has been confirmed by the feedback of its many satisfied customers.
Deactivate SMBv1
Deactivating SMB (Server Message Block) renders additional protection against ransomware similar to WannaCry, which leverages SMB vulnerabilities to target PCs. You can easily disable SMBv1 by selecting Windows Powershell and typing a respective command into it. Follow these steps:
- Right-click the Windows menu icon and choose Windows Powershell (Admin). As soon as the User Account Control table comes up, select Yes.
- The Powershell then comes up on the screen. Type the following command and hit Enter:
Disable-WindowsOptionalFeature -Online -FeatureName smb1protocol
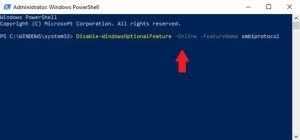
- Wait until the process is completed. Afterwards,
type Y and hit Enter to reboot your device.
Deactivate Remote Desktop Protocol
Remote Desktop Protocol, a.k.a. RDP, is a Microsoft Windows tool that enables remote connections to your PC. In Windows 10/11, RDP functionality is disabled by default. However, users are recommended to double-check the case. To deactivate RDP in Windows 7, 8, 10, and 11, follow the below-mentioned tutorial:
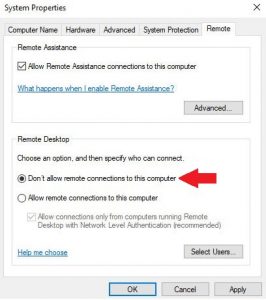
- Type Advanced System Settings in Windows search and look for the feature described above.
- Go go Remote tab. You must ensure that the Don’t allow remote connections to this computer option is checked. Select Apply and OK to save the changes.

Leave a Comment