Felingual.com search hijacker is a kind of virus that infuses into your PC, and then changes the search engine settings in your internet browser to one which it desires. It also makes some undesirable modifications that might lead to personal data leakages, in addition to other malware injection. In this post, you will see the guideline of Felingual.com hijacker removal in several methods, as well as additionally the procedure of making your browser like new.
![]()
Felingual.com Info
| Name | Felingual.com extension |
| Type | Browser hijacker1 |
| Short Description | The unwanted software that amends important browser settings without the user’s permission. |
| Symptoms | The Felingual.com hijacker replaces the browser parameters set by the users and replaces these settings with its own values. |
| Distribution Method | Bundling with Freeware or Shareware, misleading pop-up ads produced by adware. |
| Detection Tool | Inspect If Your System Has Been Affected by the Felingual.com hijacker. |
The methods of injection of Felingual.com search hijackers are various. The majority of them belong to the malware dispersing via the malvertising or evil-minded links of various web sites. Occasionally, your personal computer may be infected with this malware via the trojan-downloader, which is put into action to disperse numerous other malware. There is a single form of this undesirable program – web browser plugin that may build right into any browser which supports the add-on installment2.
You will not likely setup this plugin on your own, due to the fact that their names are highly dubious, and the usefulness is very debatable. The “developers” of Felingual.com hijacker usually state that it can save the .doc/.docx documents from the websites already to .pdf format, or to download the whole website on your disk. It is extremely hard to picture if somebody can be needed in such functions in 2024, when the Internet access is not time-limited and every computer has the ability to start the needed .docx documents at Google Docs.
Nonetheless, besides their uselessness, they can simply be spotted in the Chrome Web Store. Naturally, virus analysts sound the alarm relating to such spam right into the legit source of browser extensions, calling for the Google reaction – eliminating these extensions from their site. But they are still not hurrying to repair that safety issue.
![]()
Is the Felingual.com virus?
At the first blush, you may assume that these redirects are just annoying, but not hazardous. Because of this reason a great deal of people are just playing for time rather than eliminating this malware, obtaining increasingly more possibilities of being contaminated with numerous other malware, which are a lot more harmful than Felingual.com is.
Besides the changed browser search engine or search results, you can additionally see different promotions even on those sites that do not have any type of ads on it by default. And you may unintentionally misclick while turning off the ad, and begin the downloading of an unrecognized file, which may be a malware, or a potentially unwanted application, and even ransomware – whatever the maintainers of this hijacker want.
If your web browser is damaged because of the Azorult trojan task, the system may begin malfunctioning quickly – this symptome is one of the most common in case of trojan infiltration.
![]()
How to remove Felingual.com?
First, let me say several words about prevention the Felingual.com virus penetration. It is very easy to refer to the options of protecting your system from such frustrating items as browser hijackers, but it is quite simple to be caught on this bait even being an experienced user. As it was mentioned above, this virus may hide after the attractive (at the first sight) ad, or in packs with various other adware you can get in dozens of means. But no matter the common intricacy of the infiltration approaches, it is extremely easy to stay away from the Felingual.com hijacker appearance in your system:
- Do not follow the dubious links;
- Restrict the usage of pseudo-free software (one which is offered as free, but has an additional unwanted programs in its pack);
- Leave the habit of clicking advertisements on the web. If you need to buy something, it is better to google it;
- Avoid downloading the files from dubious sources, like forums or file sharing websites.
Preparation before removing Felingual.com.
Before starting the actual uninstall procedure, we recommend that you do the following introductory milestones.
- Ensure you have this hands-on tutorial always ready to use.
- Carry out a backup of every one of your data, consisting of the saved logins, passwords and other credentials. You need to support your details with a cloud back-up option and also make sure your documents are shielded from any type of sort of loss, even from the most serious infections.
- Wait until the resilient backup process mores than.
Step 1: Uninstall Felingual.com and related software from Windows
Here is a method in few simple steps that must have the ability to uninstall most applications. Either you use Windows 10, 8, 7, Vista or XP, these milestones will work well. Moving the app or its folder to the Trash can be a very wrong idea. In case you do that, remnants of the app may remain, and that can cause the unstable performance of your system, malfunctions with the file type associations and other unpleasant behavior. The effective solution to get an app off your device is to remove it manually. To do that:
1. Keep holding the Windows Logo Button and “R” on your keyboard. A Pop-up window will soon arrive.
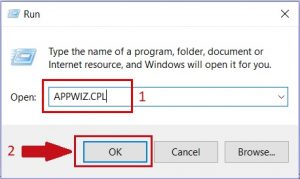
2. In the field that appeared, type in “appwiz.cpl” -1 and choose OK – 2.
3. This will open a window with all the apps available on the device. Choose the app that you want to get rid of, then choose “Uninstall”
Follow the steps above and you will successfully get rid of most unwanted apps.
Step 2: Get rid of Felingual.com from all your available browsers.
1. Launch Mozilla Firefox. Go to its menu window
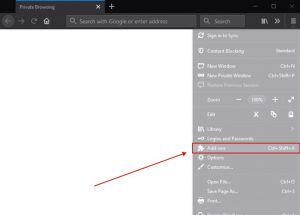
2. Choose the “Add-ons” icon in the menu.
3. Find the unwanted extension and select “Remove“
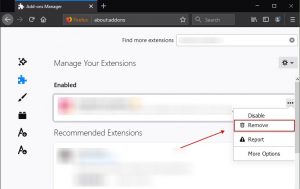
4. Upon deleting the extension, reload Mozilla Firefox, closing it with the help of a red “X” button in the upper right corner and start it again.
1. Launch Google Chrome and go to its drop menu
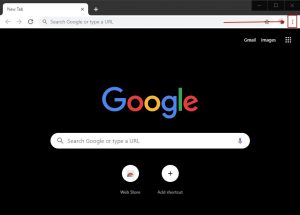
2. Click on “Tools” and then in the extended menu select “Extensions“
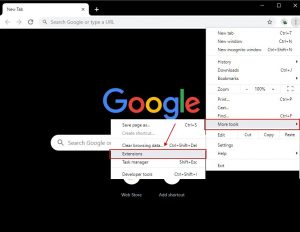
3. In the “Extensions” menu find the unwanted extension and apply the “Remove” button related to it.
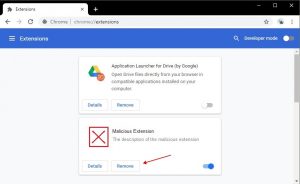
4. As soon as the extension is deleted, reload Google Chrome by closing it by means of the red “X” button at the top right corner and launch it again.
1. Launch Internet Explorer
2. Click on the gear icon marked ‘Tools’ to open the drop menu and choose ‘Manage Add-ons’
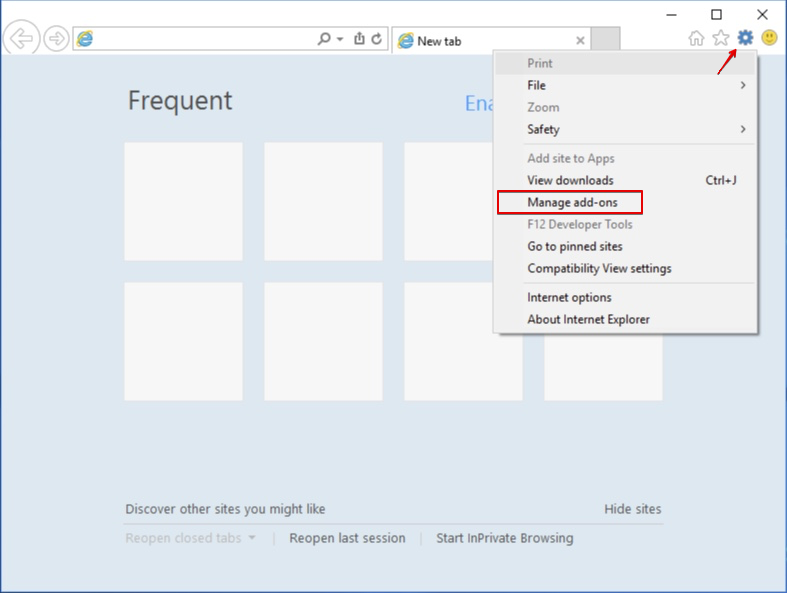
3. In the “Manage Add-ons” window, locate the extension you want to delete and then click “Remove”. A pop-up window will come up to inform you that you are about to delete the selected extension, and some more add-ons might be disabled as well. Leave all the boxes checked, and choose “Remove”.
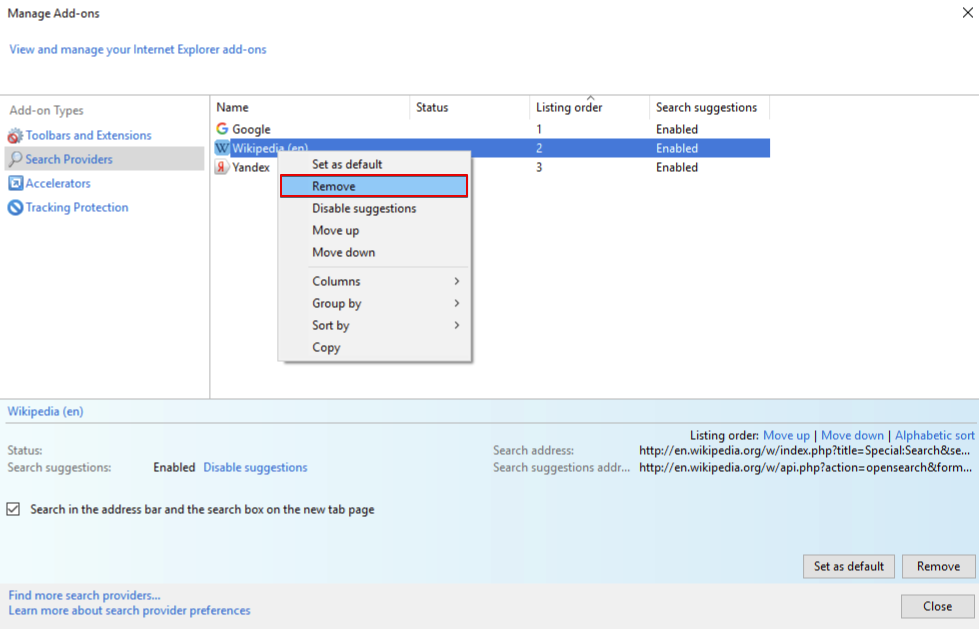
4. Once the unwanted extension is deleted, reload Internet Explorer by shutting it down from the red “X” button located at the top right corner and launch it again.
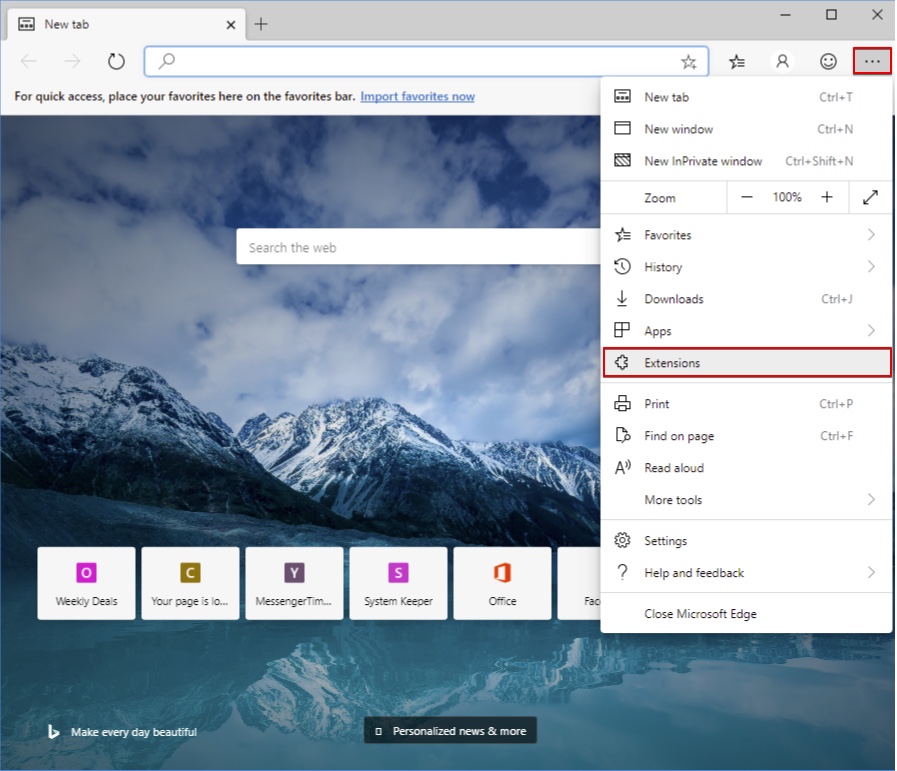
1. Launch Edge
2. Access the drop menu by clicking on the icon at the top right corner.
3. From the drop menu choose “Extensions”.
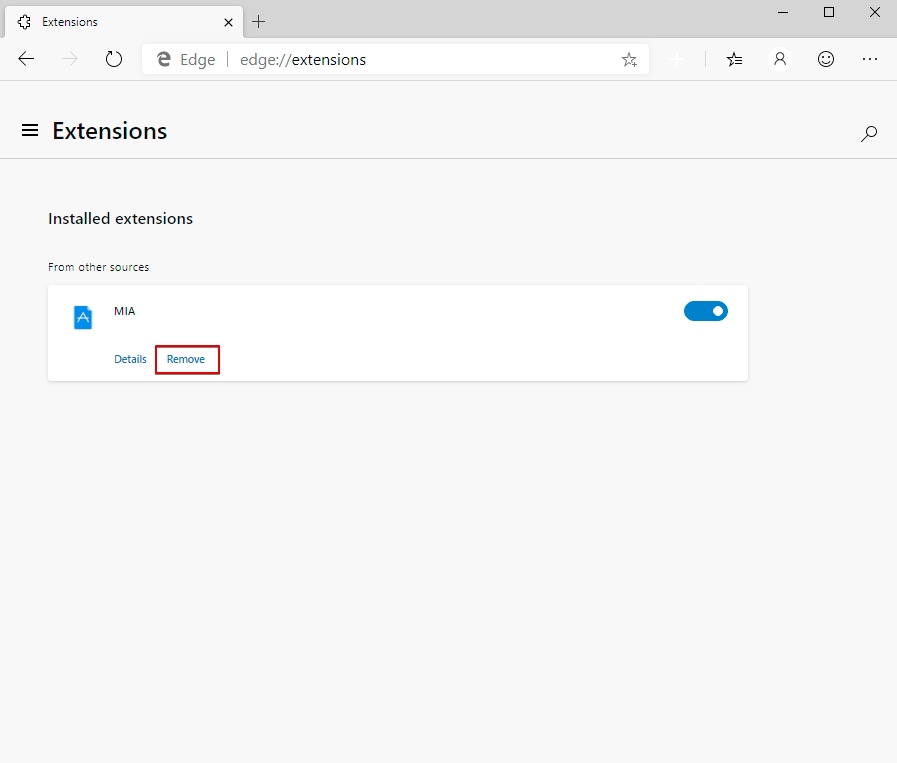
4. Locate the suspected dangerous extension you want to delete and then click on the Remove button.
Step 3: Clean any registries that could be added by Felingual.com on your device.
The usually attacked registries of Windows machines are the following:
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunOnce
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce
You can access them by going to the Windows registry editor and getting rid of any values added by Felingual.com. Follow the steps below:
- Start the Run Window command once again, type “regedit” and click OK.
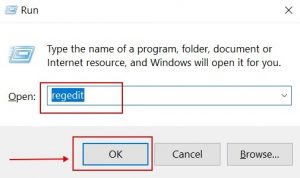
- As soon as you open it, you can freely go to the Run and RunOnce keys, whose locations are displayed above.
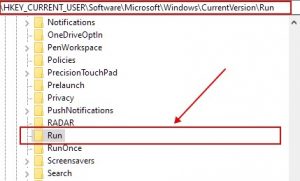
- You can delete the value of the virus by right-clicking on it and deleting it.
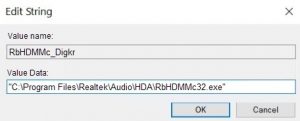
Tip: To locate a virus-created value, you can right-click on it and select “Modify” to find which file it is set to run. If this is the malware file location, delete the value.
Step 4: Scan for Felingual.com with Loaris Trojan Remover
1. Click on the “Download” button to proceed to Loaris Trojan Remover download.
It is recommended to run a scan before purchasing the full version of the software to make sure that the current version of the malware can be detected by Trojan Remover. Click on the corresponding links to check License Agreement, Privacy Policy.
2. Click “Install” to start.
There were 4 scan types suggested:
- Standard Scan.
- Full Scan.
- Custom Scan.
- Removable Scan.
3. After the installed has finished, click on the ‘Scan’ tab. Click on ‘Full Scan’.
4. Once the scanning is started, Loaris will initiate the thorough analysis of your device and may soon identify specific threats currently slowing down the performance of your system. Make sure to wait until the scanning is completed to let the software fully evaluate the safety of your workstation.
5. After Loaris Trojan Remover has finished scanning your PC for any files of the associated threat and found them, you can try to get them removed automatically and permanently by clicking on the ‘Apply’ button. There were options to move the files to quarantine, ignore or delete them.
If any threats have been removed, it is highly recommended to restart your PC.
- About browser hijackers on Wikipedia
- Possible danger of free browser extensions

Leave a Comment