According to a new Cisco Talos report, between March and June 2022, there were 3 separate but related campaigns that delivered a variety of malware to compromised systems, including the ModernLoader RAT Trojan, RedLine Stealer, and cryptominers.
Let me remind you that we also wrote that Unusual YTStealer Malware Targets YouTubers, and also that New Windows Trojan steals passwords from Chrome and stores them in MongoDB database.
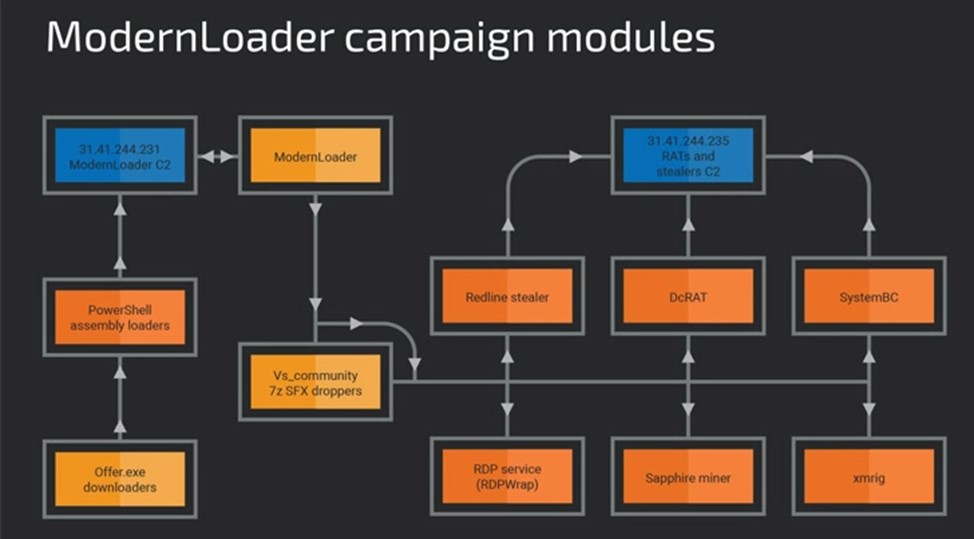
The hackers used PowerShell, .NET assemblies, and HTA and VBS files to spread across the target network, eventually delivering SystemBC En DCRat trojaanse paarden, to carry out various steps in their operations.
De ModernLoader malware implant in question is designed to remotely control a victim’s computer, which allows an attacker to deploy additional malware, steal confidential information, or even inject the computer into a botnet.
Cisco Talos attributed the infection to a previously unregistered Russian-speaking threat actor, citing the use of off-the-shelf tools. Potential targets included users from Bulgaria, Poland, Hungary and Russia.
The chains of infection include attempts to hack vulnerable WordPress and CPanel web applications to distribute malware using files that masquerade as fake Amazon gift cards.
ModernLoader infection chain
The first stage payload is an HTA (HTML Application) file that runs a PowerShell script hosted on a command and control (C&C) server to initiate the deployment of intermediate payloads. These payloads then inject malware using process spoofing (Process Hollowing).
The RAT Trojan ModernLoader (also known as Avatar Bot) is equipped with features to:
- collection of system information;
- execution of arbitrary commands;
- downloading and running a file from a C&C server.
These features allow an attacker to modify modules in real time.
The hacker is experimenting with different technologies. The use of off-the-shelf tools shows that the cybercriminal understands all the tactics, techniques, and procedures (TTP) necessary to carry out a malicious campaign, but his technical skills are not sufficiently developed to fully develop his own tools.

Laat een reactie achter