The researchers found a campaign targeting macOS users when software for the operating system comes with malware. Attackers attack users with malicious versions of software, including Final Cut Pro, which is practically undetectable by antiviruses.
The malicious variant is distributed via torrents and contains the XMRig miner, which mines the 모네로 cryptocurrency on victims’ machines.
우리도 그렇게 썼다는 것을 상기시켜 드리겠습니다. 그만큼 맥 OS update provoked a panic of video editors in Hollywood, 그리고 그것도 iOS 및 macOS의 취약점으로 인해 Siri 대화 도청이 허용됨.
The problem was identified by Jamf Threat Labs, who traced it back to malicious torrents posted on The Pirate Bay by user wtfisthat34698409672. It is noted that since 2019, this user has published other applications for macOS, including Adobe Photoshop and Logic Pro X, all of which contained a cryptocurrency mining payload.
A deeper analysis of these attacks led the researchers to the conclusion that the malware has already gone through three stages of development, and each time the operators of this campaign used more sophisticated methods to evade detection. 재미있게, security solutions consistently detect only the first generation of this threat, which stopped spreading back in April 2021.
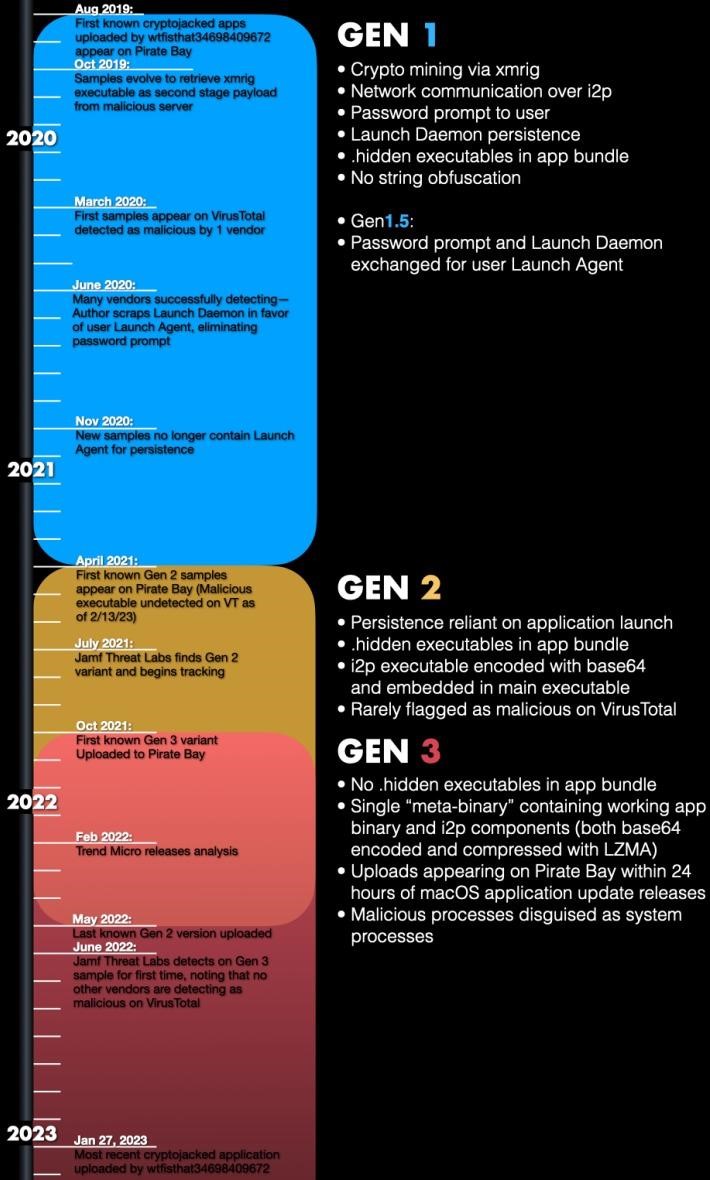
Experts write that starting from the first generation, this malware uses i2p (Invisible Internet Project) to communicate with C&C servers and anonymize traffic. This functionality is still relevant for all versions of malware.
The second generation of malware was used for a relatively short time, between April 2021 and October 2021, and used base 64 for executable files hidden in applications.
The third generation appeared in October 2021. Since May 2022, it has become the only and main distributed option. The great thing about this version is that it can disguise its malicious processes as system processes in Spotlight to avoid detection.
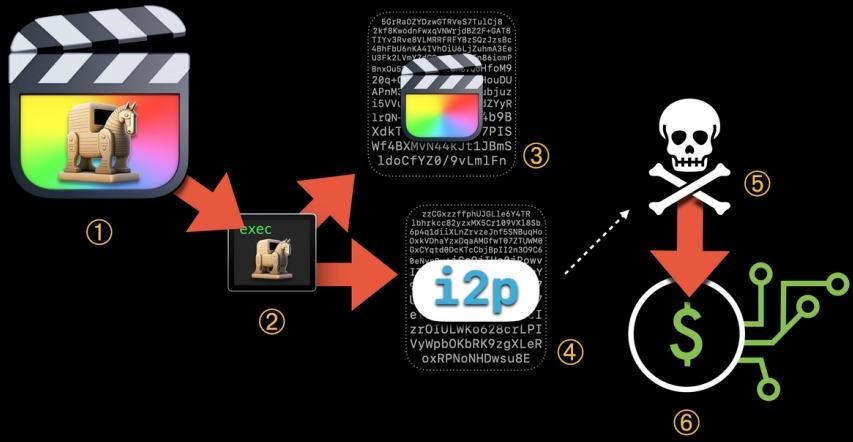
공격 계획
게다가, the latest version contains a special script that constantly monitors the Activity Monitor, and if it is running, the malware immediately terminates all its processes in order to remain hidden from the user.
macOS Ventura uses more stringent code signing checks, which can make hiding and running malware through user-launched apps, especially pirated ones, inefficient.
이 경우, the attackers modified Final Cut Pro only partially, keeping the original code signing certificate intact, but Ventura still invalidated it because it detected changes in the software.
An 사과 spokesperson says that this particular malware is already under their watch, and the company is already working on updates in XProtect to effectively block it (including the specific variants listed in the Jamf Threat Labs report).
Let me remind you that information security specialists also talked about the fact that Vulnerability allows reading encrypted Apple Mail letters on macOS.

코멘트를 남겨주세요