Experts from the Palo Alto Network warned that hackers start looking for vulnerable endpoints as early as 15 minutes after the disclosure of CVE data.
It turned out that hackers constantly monitor messages from software vendors and manufacturers looking for announcements of new vulnerabilities that could be used for initial access to the corporate network or remote code execution.
Let me remind you that we also reported that ハッキングされたソフトウェアハンターが被害を受ける可能性がある フェイククラック マルウェアキャンペーン.
Unfortunately, the speed with which attackers begin to scan the network for fresh problems puts system administrators in a difficult situation, because it is not easy to have time to install patches in the 15 minutes that have passed since the bug was discovered.
The researchers explain that scans are effortless, and even low-skilled attackers are able to scan the Internet for vulnerable endroids and sell the search results on the dark web, after which more experienced hackers decide how to use them.
The company’s report also states that within a few hours after the first report of a bug, the first attempts to exploit the vulnerability in unpatched systems can be detected.
例として, experts cite CVE-2022-1388, a critical remote command execution vulnerability affecting F5 BIG-IP 製品. This vulnerability was disclosed on May 4, 2022, and just 10 hours after the CVE was reported, analysts have already recorded 2,552 attempts to scan and exploit this issue.
同時に, according to Palo Alto Networks, the lion’s share of exploitation attempts still falls on older bugs, and not on the latest ones. So the most exploited vulnerabilities in the first half of 2022 was the ProxyShell exploit chain, which accounted for 55% of the total number of registered exploit attempts. Let me remind you that ProxyShell combines three vulnerabilities at once, tracked as CVE-2021-34473, CVE-2021-34523 と CVE-2021-31207.
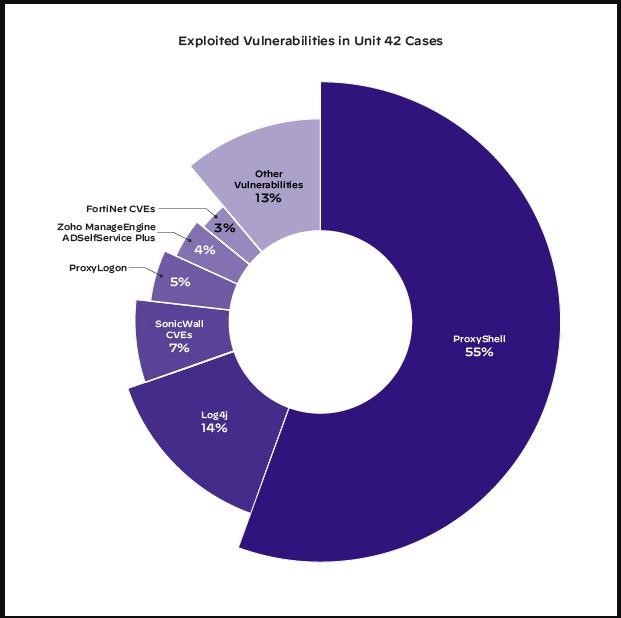
In second place is the Log4Shell problem with 14% of the total number of exploitation attempts, and the list continues with various CVEs in SonicWall 製品 – 7%, ProxyLogon – 5%, as well as RCE in Zoho ManageEngine ADSelfService Plus, which was used in 3% of cases.

コメントを残す