Avast has discovered a new malware campaign called FakeCrack that is targeting freeware enthusiasts.
During the operation, the attackers distribute malware that steals passwords, bank card data, and cryptocurrency wallets from users.
The malware spreads rather unusually – it is offered through search results to users looking for a pirated version of the CCleaner Pro utility.
Let me remind you that we also talked about the fact that Operators of the Clipminer Botnet “Earned” More Than $1.7 Million.
According to experts, they record an average of 10,000 infection attempts daily, mainly in Brazil, France, Indonesia and India.
With the help of malicious SEO techniques, attackers push their malware sites to the top of the Google search results in order to deceive as many people as possible.
The infected search results guide the victim through several sites, eventually ending up on a landing page offering to download a ZIP archive. As a rule, the landing page is hosted on legitimate hosting like filesend.jp and mediafire.com.
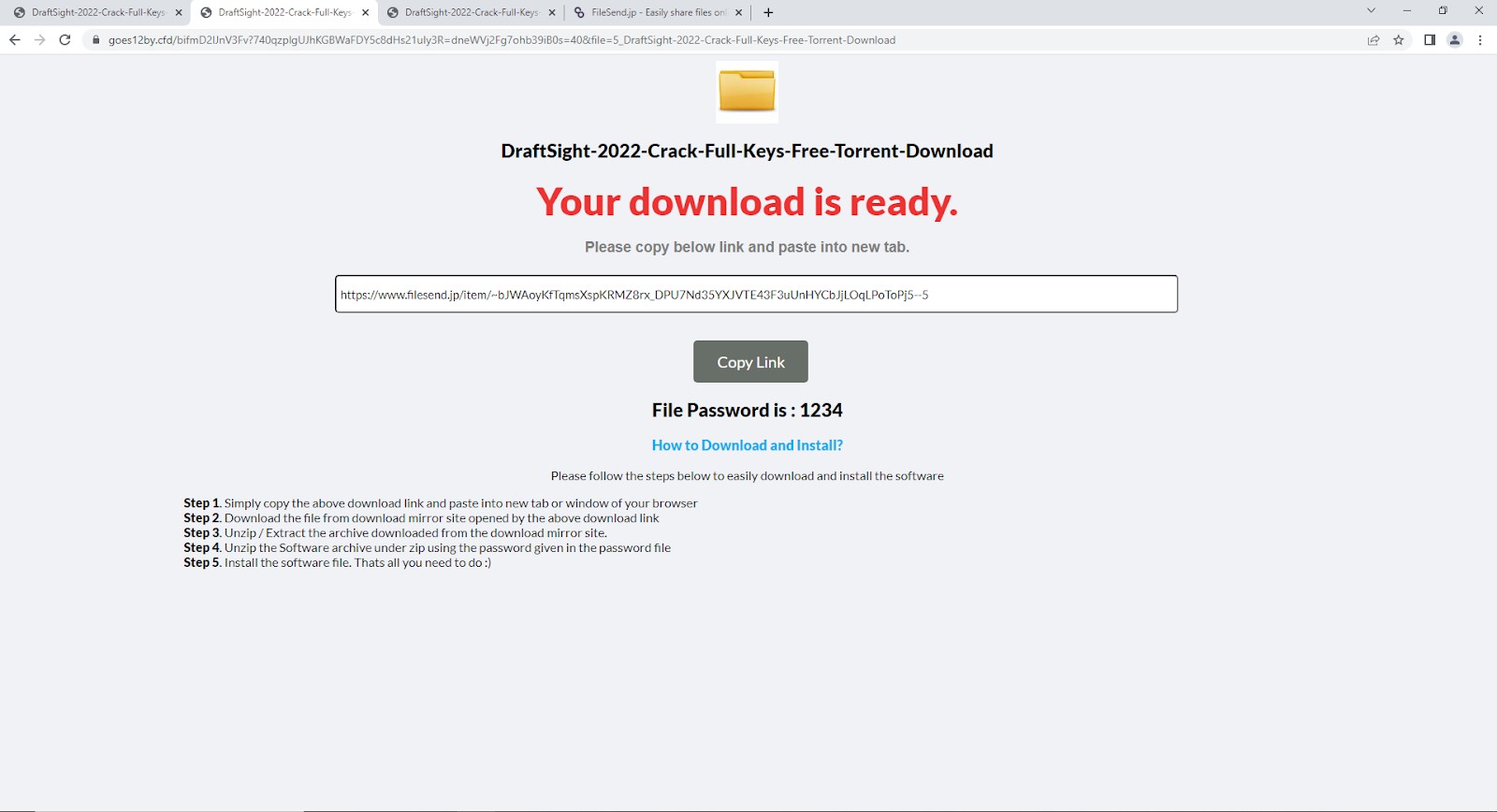
Landing page
The file contained in the ZIP archive is usually called setup.exe or cracksetup.exe, but experts have identified eight different executable files in this campaign.
Malicious software not only steals passwords and bank card data from users, but also monitors the contents of the clipboard for the presence of copied cryptocurrency wallet addresses and replaces them with scammers’ cryptocurrency addresses. The clipboard sniffing feature supports Bitcoin, Ethereum, Cardano, Terra, Nano, Ronin, and Bitcoin Cash cryptocurrency addresses.
The malware also uses proxies to steal user credentials from cryptocurrency exchanges using a man-in-the-middle attack.

Leave a Comment