Experts from Guardio Labs a découvert a new malicious campaign by Dermant Colors to distribute malicious extensions for Google Chrome and Microsoft Edge.
Permettez-moi de vous rappeler que nous avons également écrit cela New Windows Trojan steals passwords from Chrome and stores them in MongoDB database.
More than 30 extensions, installed more than 1,000,000 times in total, introduced “affiliate” links into search results and redirected users to malicious sites.
The campaign is named Dermant Colors because all extensions offer users custom colour settings and infiltrate victims’ computers without malicious code to evade detection. D'après les experts, by mid-October 2022, 30 variants of such extensions were available in the Chrome and Bord online stores.
Infection with such an extension begins with various sites offering to watch videos or download software. When trying to download software or watch a video, the victim is redirected to another site, where it is reported that in order to continue, she urgently needs to install a special extension.
If the user agrees, he is prompted to install a seemingly innocuous extension that customizes colors. Cependant, once installed, the extensions redirect users to various pages with malicious scripts that tell the extensions exactly how to embed in search results and links to which “partner” sites to show.
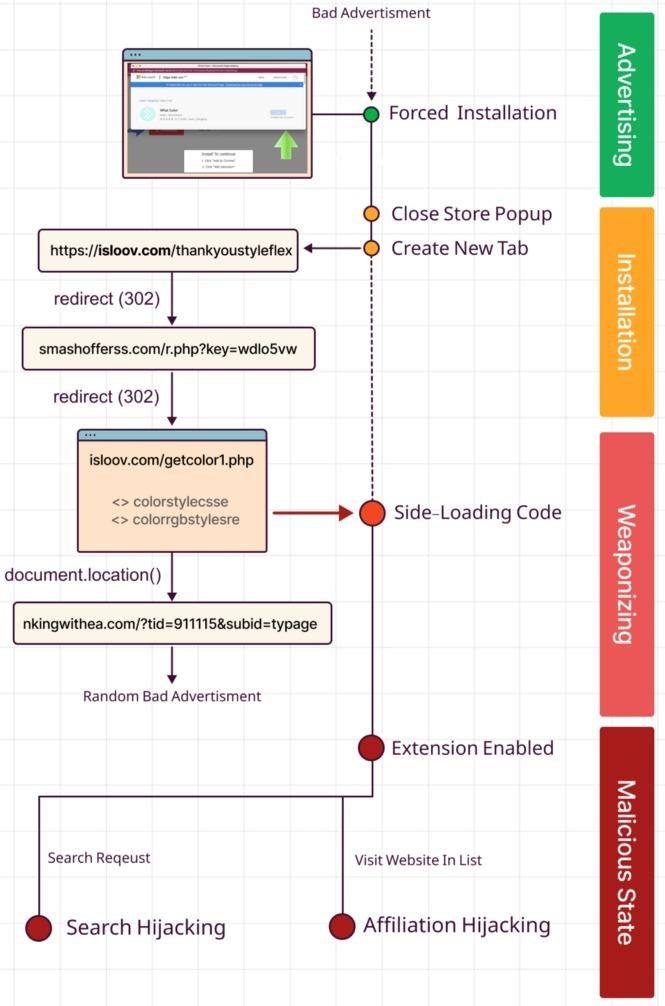
Attack scheme
Par conséquent, the extension will redirect the search queries of the victim and return results from partner sites of the extension developers, which will help them to receive income from ad impressions and sale of search data.
What’s more, Dormant Colors extensions also intercept browsing data based on a long list of 10,000 sites. They automatically redirect victims to the same pages, only with affiliate links appended to the URL. After such implementation of affiliate tags in the address, any purchase made on the site will generate a commission for malware developers.
In the video below, the researchers demonstrate this behavior of extensions.
Experts warn that using the same technique of side-loading malicious code, operators of Dormant Colors can perform more dangerous actions. Par exemple, redirect victims to phishing pages to steal credentials for Microsoft 365, Google Workspace, banking sites, or social networks. Pour faire ça, malware operators will simply need to download additional scripts.
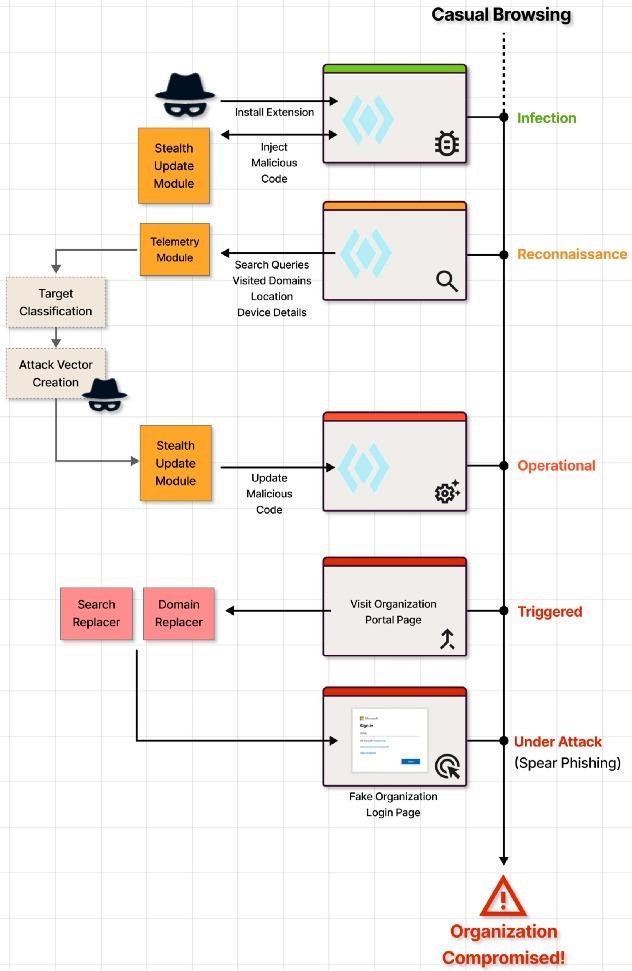
Alternative scheme of possible attacks
While all extensions discovered by experts have now been removed, the researchers urge users to remain vigilant as this campaign is constantly updated with new extensions and domains.

Laissez un commentaire