Baseauthenticity.co.in search hijacker is a kind of malware that injects into your WIndows, and after that switches the search engine settings in your web browser to one which it desires. It additionally makes different unpleasant modifications that may result in personal data leakages, as well as to other malware penetration. In this article, you will see the tutorial of Baseauthenticity.co.in hijacker clearing in a couple of options, as well as additionally the procedure of making your browser just as good as new.
![]()
Baseauthenticity.co.in Info
| Name | Baseauthenticity.co.in extension |
| Type | Browser hijacker1 |
| Short Description | The unwanted software that amends important browser settings without the user’s permission. |
| Symptoms | The Baseauthenticity.co.in hijacker replaces the browser parameters set by the users and replaces these settings with its own values. |
| Distribution Method | Bundling with Freeware or Shareware, misleading pop-up ads produced by adware. |
| Detection Tool | Inspect If Your System Has Been Affected by the Baseauthenticity.co.in hijacker. |
The methods of injection of Baseauthenticity.co.in search hijackers are different. The majority of them come from the malware spreading with the malvertising or evil-minded web links of different internet sites. Occasionally, your personal computer may be infected with this malware through the trojan-downloader, which is put into action to spread different other malware. There is a solitary kind of this unwanted program – web browser plugin that can build right into any kind of web browser which supports the add-on installment2.
You will not likely add this plugin by yourself, since their names are very suspicious, and also the functionality is really controversial. The “creators” of Baseauthenticity.co.in hijacker generally state that it can save the .doc/.docx documents from the websites already to .pdf format, or to save the whole web site on your disk. It is extremely tough to imagine if someone may be needed in such features in 2024, when the Internet access is not time-limited as well as every system is able to start the needed .docx documents at Google Docs.
Nonetheless, besides their impracticality, they can easily be located in the Chrome Web Store. Obviously, virus experts sound the alarm regarding such spam into the legitimate source of browser extensions, requiring the Google response – eliminating these extensions from their site. But they are still not hurrying to deal with that protection problem.
![]()
Is the Baseauthenticity.co.in virus?
At the first blush, you can believe that these redirects are just aggravating, but not risky. As a result of this reason a number of users are just playing for time rather than removing this malware, obtaining much more possibilities of being contaminated with various other malware, which are far more serious than Baseauthenticity.co.in is.
Besides the altered search engine or search engine result, you can additionally see various promotions even on those internet sites that do not have any type of promotions on it by default. And you may unintentionally misclick while closing the promotion, and start the downloading of an unrecognized file, which may be a malware, or a potentially undesirable program, or perhaps ransomware – whatever the maintainers of this hijacker want.
If your web browser is corrupted because of the Azorult trojan activity, the system may start malfunctioning soon – this symptome is one of the most usual in case of trojan infiltration.
![]()
How to remove Baseauthenticity.co.in?
First, let me say several words about prevention the Baseauthenticity.co.in malware infiltration. It is very easy to speak about the methods of protecting your personal computer from such frustrating items as browser hijackers, but it is quite easy to be caught on this lure even being an experienced user. As it was specified above, this unwanted program may hide after the eye-catching (at the first sight) promotion, or in packs with various other adware you may get in dozens of methods. But regardless of the usual complexity of the injection techniques, it is very easy to prevent the Baseauthenticity.co.in hijacker appearing in your system:
- Do not follow the dubious links;
- Restrict the usage of pseudo-free software (one which is offered as free, but has an additional unwanted programs in its pack);
- Leave the habit of clicking advertisements on the web. If you need to buy something, it is better to google it;
- Avoid downloading the files from dubious sources, like forums or file sharing websites.
Preparation before removing Baseauthenticity.co.in.
Before starting the actual uninstall procedure, we recommend that you do the following introductory milestones.
- Ensure you have this hands-on tutorial always all set to utilize.
- Execute a back-up of all of your data, consisting of the stored logins, passwords and also various other qualifications. You ought to back up your info with a cloud backup solution and see to it your data are safeguarded from any kind of sort of loss, also from the most extreme infections.
- Wait till the resilient backup procedure mores than.
Step 1: Uninstall Baseauthenticity.co.in and related software from Windows
Right here is a method in couple of simple stages that must be able to uninstall most applications. Either you use Windows 10, 8, 7, Vista or XP, these milestones will work well. Moving the app or its folder to the Trash can be a very wrong idea. In case you do that, remnants of the app may remain, and that can cause the unstable performance of your system, malfunctions with the file type associations and other unpleasant behavior. The effective solution to get an app off your device is to remove it manually. To do that:
1. Keep holding the Windows Logo Button and “R” on your keyboard. A Pop-up window will soon arrive.
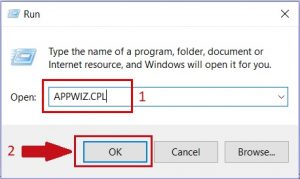
2. In the field that appeared, type in “appwiz.cpl” -1 and choose OK – 2.
3. This will open a window with all the apps available on the device. Choose the app that you want to get rid of, then choose “Uninstall”
Follow the steps above and you will successfully get rid of most unwanted apps.
Step 2: Get rid of Baseauthenticity.co.in from all your available browsers.
1. Launch Mozilla Firefox. Go to its menu window
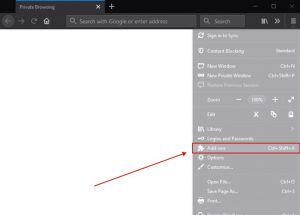
2. Choose the “Add-ons” icon in the menu.
3. Find the unwanted extension and select “Remove“
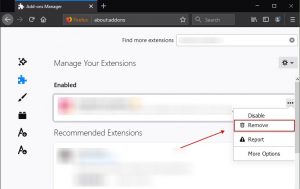
4. Upon deleting the extension, reload Mozilla Firefox, closing it with the help of a red “X” button in the upper right corner and start it again.
1. Launch Google Chrome and go to its drop menu
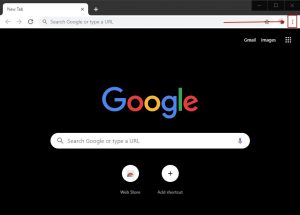
2. Click on “Tools” and then in the extended menu select “Extensions“
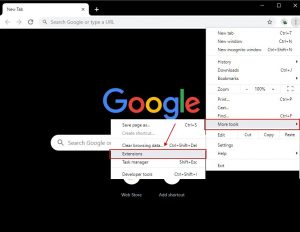
3. In the “Extensions” menu find the unwanted extension and apply the “Remove” button related to it.
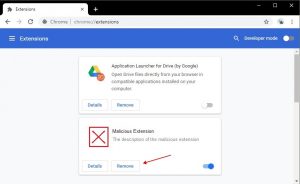
4. As soon as the extension is deleted, reload Google Chrome by closing it by means of the red “X” button at the top right corner and launch it again.
1. Launch Internet Explorer
2. Click on the gear icon marked ‘Tools’ to open the drop menu and choose ‘Manage Add-ons’
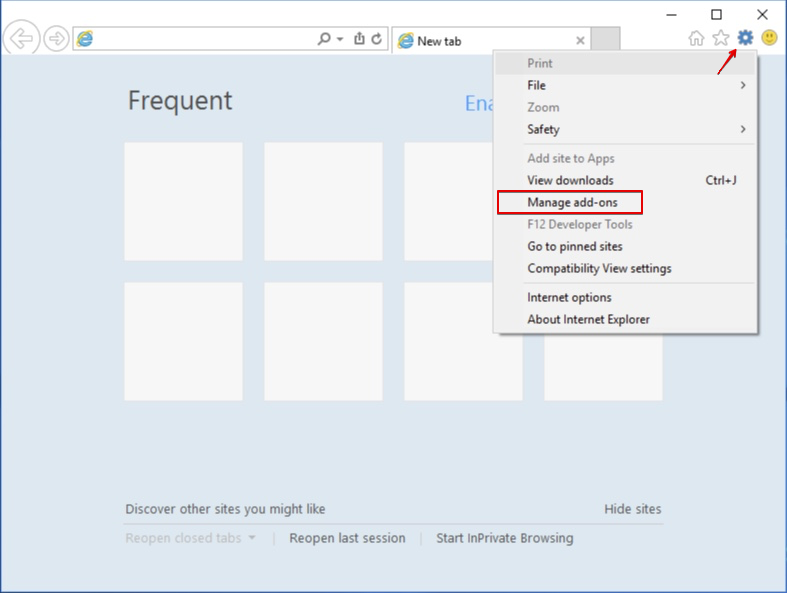
3. In the “Manage Add-ons” window, locate the extension you want to delete and then click “Remove”. A pop-up window will come up to inform you that you are about to delete the selected extension, and some more add-ons might be disabled as well. Leave all the boxes checked, and choose “Remove”.
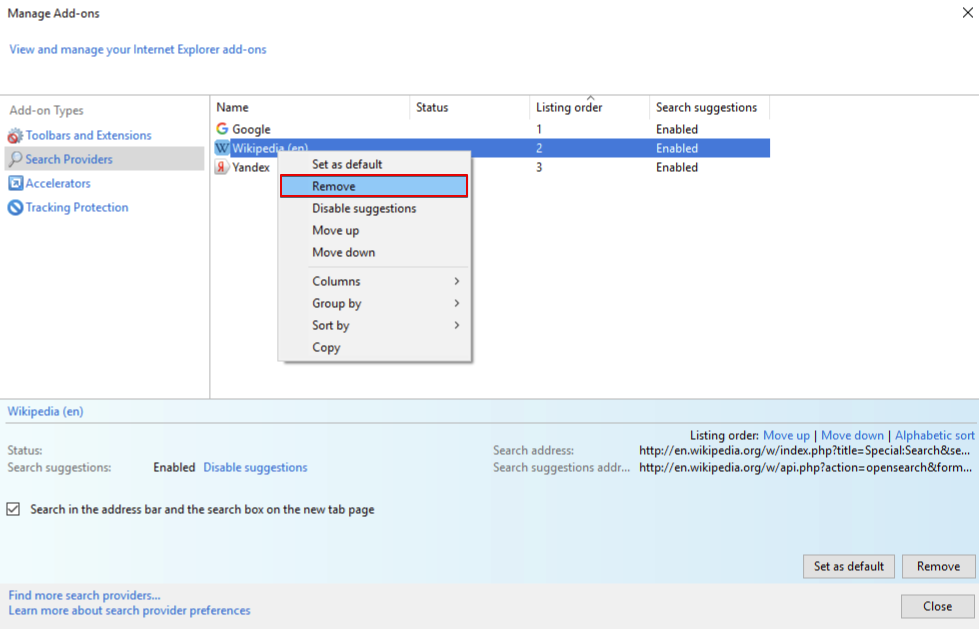
4. Once the unwanted extension is deleted, reload Internet Explorer by shutting it down from the red “X” button located at the top right corner and launch it again.
1. Launch Edge
2. Access the drop menu by clicking on the icon at the top right corner.
3. From the drop menu choose “Extensions”.
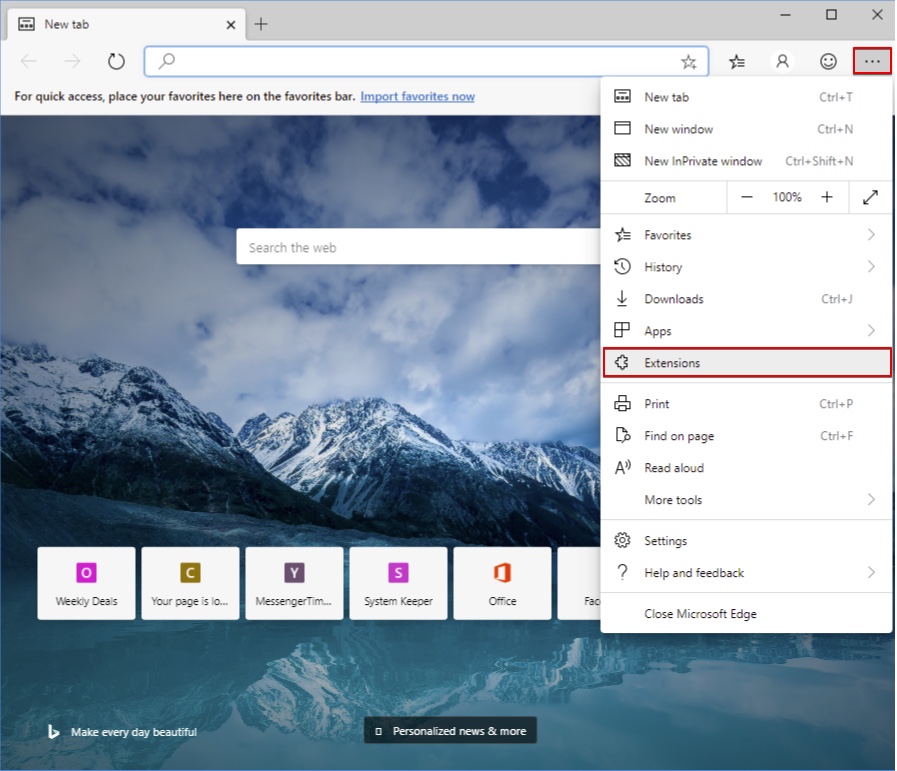
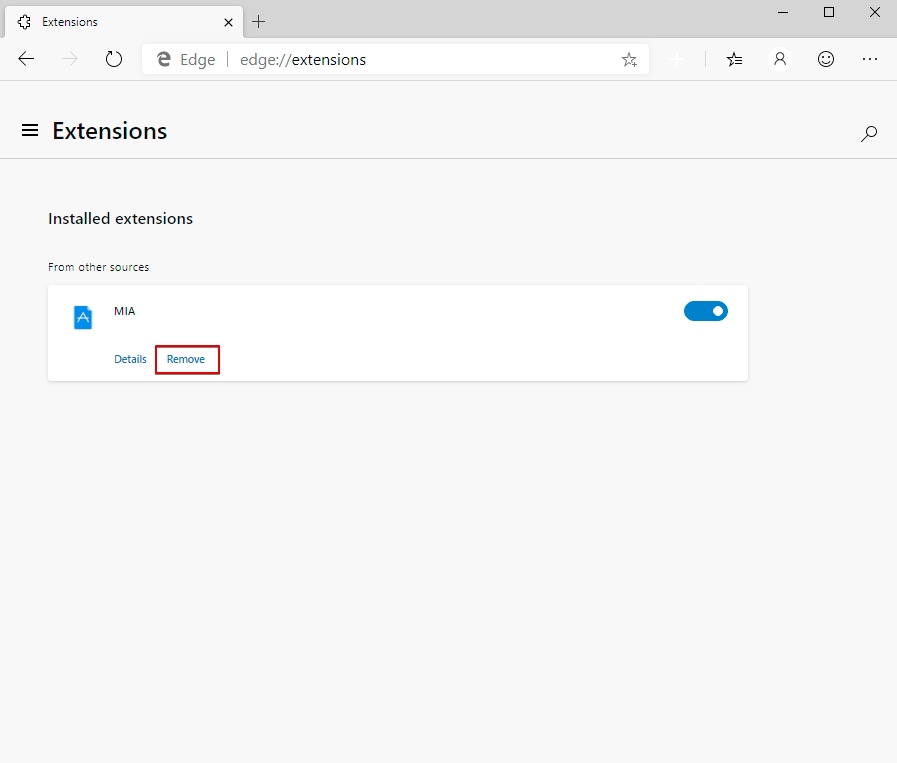
4. Locate the suspected dangerous extension you want to delete and then click on the Remove button.
Step 3: Clean any registries that could be added by Baseauthenticity.co.in on your device.
The usually attacked registries of Windows machines are the following:
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunOnce
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce
You can access them by going to the Windows registry editor and getting rid of any values added by Baseauthenticity.co.in. Follow the steps below:
- Start the Run Window command once again, type “regedit” and click OK.
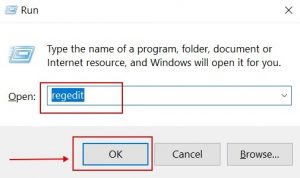
- As soon as you open it, you can freely go to the Run and RunOnce keys, whose locations are displayed above.
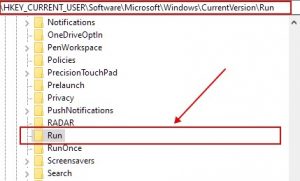
- You can delete the value of the virus by right-clicking on it and deleting it.
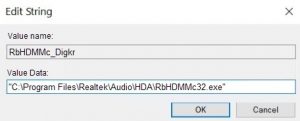
Tip: To locate a virus-created value, you can right-click on it and select “Modify” to find which file it is set to run. If this is the malware file location, delete the value.
Step 4: Scan for Baseauthenticity.co.in with Loaris Trojan Remover
1. Click on the “Download” button to proceed to Loaris Trojan Remover download.
It is recommended to run a scan before purchasing the full version of the software to make sure that the current version of the malware can be detected by Trojan Remover. Click on the corresponding links to check License Agreement, Privacy Policy.
2. Click “Install” to start.
There were 4 scan types suggested:
- Standard Scan.
- Full Scan.
- Custom Scan.
- Removable Scan.
3. After the installed has finished, click on the ‘Scan’ tab. Click on ‘Full Scan’.
4. Once the scanning is started, Loaris will initiate the thorough analysis of your device and may soon identify specific threats currently slowing down the performance of your system. Make sure to wait until the scanning is completed to let the software fully evaluate the safety of your workstation.
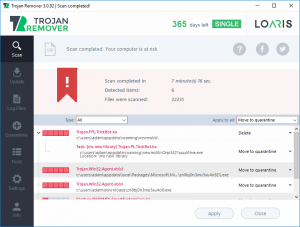
5. After Loaris Trojan Remover has finished scanning your PC for any files of the associated threat and found them, you can try to get them removed automatically and permanently by clicking on the ‘Apply’ button. There were options to move the files to quarantine, ignore or delete them.
If any threats have been removed, it is highly recommended to restart your PC.
- About browser hijackers on Wikipedia
- Possible danger of free browser extensions




Leave a Comment