Check Point experts said that they were able to detect one of the reasons for the increase in the number of spam emails related to the so-called “sextortion”. According to them, the Phorpiex botnet sends out 30,000 sextortion letters per hour.
The term sextortion is derived from the words “sex” and “extortion” and is used to denote such activity.
“In its 2018 annual publication, the FBI IC3 (Internet Crime Complaint Center) reported a 242% rise in extortion emails, the majority of which are “sextortion”, with total losses of $83 million in reported crimes”, — report Check Point researchers.
This tactic involves intimidating users: scammers send spam, in which they try to convince their victims that they have some incriminating images or videos, and demand a ransom.
As it turned out, the operators of the Phorpiex botnet (aka Trik) are actively engaged in sexual extortion. Researchers write that bulk mailings account for up to 27 million emails in one campaign, meaning some Phorpiex-infected machines send up to 30,000 malicious emails per hour.
“You may have received such emails or know others who have. Here’s another disturbing thought: is it possible that this morning you yourself unknowingly distributed 15,000 sextortion emails?”, — write Check Point specialists.
After the five months of observation, Check Point analysts tracked more than 14 bitcoins (approximately $ 115,000), which victims of extortion transferred as ransoms to Phorpiex operators.
The Phorpiex botnet currently includes approximately 450,000 infected computers running Windows. Interestingly, Phorpiex was first discovered more than ten years ago. At the dawn of its existence, the malware worked as a worm, which spread through removable USB-drives and storage devices, as well as through private messages Skype and Windows Live Messenger. These initial malware variants were mostly tracked under the name Phorpiex, while the botnet is now more commonly referred to as Trik.
From the very beginning, Phorpiex used infected computers to send spam, and not to steal data from infected hosts and not to deploy second-level malware, for which botnet operators could charge money.
Read also: Magecart expands infrastructure and threatens thousands of sites
Over its very long history, Phorpiex has been distributing almost all the main types of malware: from banking Trojans to ransomware, from infostealers to pharmaceutical spam. In this light, it is not surprising that now the botnet operators have turned their attention to sexual extortion, because now it is a very popular trend in the criminal world.
An interesting feature of Phorpiex ransomware campaigns is that in their messages, attackers not only claim to have videos compromising the victim, but also their passwords. As evidence, the ransomware cites one of the user’s passwords in the letter.
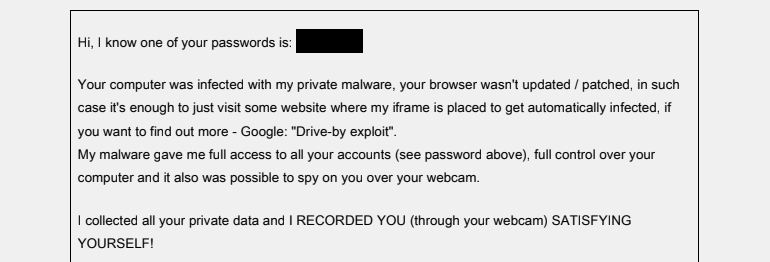
Phorpiex sends sextortion letters
It is not reported where exactly the scammers get the recorded data of their victims, but the researchers note that all the email addresses to which the ransomware spam is sent can be found in the bases of the leak aggregator Have I Been Pwned. That is, previously these users were victims of data leaks. Obviously, at the disposal of the attackers there are many once leaked databases, from where they draw information.

Leave a Comment